Alleged Spam King Pyotr Levashov Arrested
Authorities in Spain have arrested a Russian computer programmer thought to be one of the world’s most notorious spam kingpins.
Spanish police arrested Pyotr Levashov under an international warrant executed in the city of Barcelona, according to Reuters. Russian state-run television station RT (formerly Russia Today) reported that Levashov was arrested while vacationing in Spain with his family.
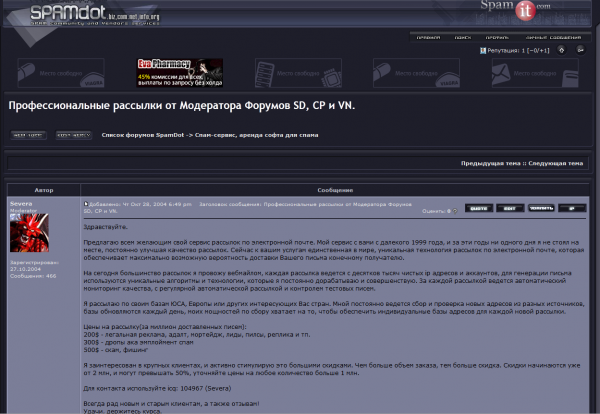
According to numerous stories here at KrebsOnSecurity, Levashov was better known as “Severa,” the hacker moniker used by a pivotal figure in many Russian-language cybercrime forums. Severa was the moderator for the spam subsection of multiple online communities, and in this role served as the virtual linchpin connecting virus writers with huge spam networks — including some that Severa allegedly created and sold himself.
Levashov is currently listed as #7 in the the world’s Top 10 Worst Spammers list maintained by anti-spam group Spamhaus. The U.S. Justice Department maintains that Severa was the Russian partner of Alan Ralsky, a convicted American spammer who specialized in “pump-and-dump” spam schemes designed to artificially inflate the value of penny stocks.
Levashov allegedly went by the aliases Peter Severa and Peter of the North (Pyotr is the Russian form of Peter). My reporting indicates that — in addition to spamming activities — Severa was responsible for running multiple criminal operations that paid virus writers and spammers to install “fake antivirus” software. So-called “fake AV” uses malware and/or programming tricks to bombard the victim with misleading alerts about security threats, hijacking the PC until its owner either pays for a license to the bogus security software or figures out how to remove the invasive program.
A screenshot of a fake antivirus or “scareware” affiliate program run by “Severa,” allegedly the cybercriminal alias of Pyotr Levashov.
There is ample evidence that Severa is the cybercriminal behind the Waledac spam botnet, a spam engine that for several years infected between 70,000 and 90,000 computers and was capable of sending approximately 1.5 billion spam messages a day.
In 2010, Microsoft launched a combined technical and legal sneak attack on the Waledac botnet, successfully dismantling it. The company would later do the same to the Kelihos botnet, a global spam machine which shared a great deal of computer code with Waledac.
The connection between Waledac/Kelihos and Severa is supported by data leaked in 2010 after hackers broke into the servers of pharmacy spam affiliate program SpamIt. According to the stolen SpamIt records, Severa — this time using the alias “Viktor Sergeevich Ivashov” — brought in revenues of $438,000 and earned commissions of $145,000 spamming rogue online pharmacy sites over a 3-year period.
Severa also was a moderator of Spamdot.biz (pictured in the first screenshot above), a vetted, members-only forum that at one time attracted almost daily visits from most of Russia’s top spammers. Leaked Spamdot forum posts for Severa indicate that he hails from Saint Petersburg, Russia’s second-largest city.
According to an exhaustive analysis published in my book — Spam Nation: The Inside Story of Organized Cybercrime — Severa likely made more money renting Waledac and other custom spam botnets to other spammers than blasting out junk email on his own. For $200, vetted users could hire one of his botnets to send 1 million pieces of spam. Junk email campaigns touting auction and employment scams cost $300 per million, and phishing emails designed to separate unwary email users from their usernames and passwords could be blasted out through Severa’s botnet for the bargain price of $500 per million.
The above-referenced Reuters story on Levashov’s arrest cited reporting from Russian news outlet RT which associated Levashov with hacking attacks linked to alleged interference in last year’s U.S. election. But subsequent updates from Reuters cast doubt on those claims.
“A U.S. Department of Justice official said it was a criminal matter without an apparent national security connection,” Reuters added in an update to an earlier version of its story.
The New York Times reports that Russian news media did not say if Levashov was suspected of being involved in that activity. However, The Times piece observes that the Kelihos botnet does have a historic association with election meddling, noting the botnet was used during the Russian election in 2012 to send political messages to email accounts on computers with Russian Internet addresses. According to The Times, those emails linked to fake news stories saying that Mikhail D. Prokhorov, a businessman who was running for president against Vladimir V. Putin, had come out as gay.
Source: krebsonsecurity.com
 Reviewed by Anonymous
on
9:29 PM
Rating:
Reviewed by Anonymous
on
9:29 PM
Rating: