D-Link MEA Site Caught Running Cryptocurrency Mining Script—Or Was It Hacked?
Last month the popular torrent website The Pirate Bay caused some uproar by adding a Javascript-based cryptocurrency miner to its site with no opt-out option, utilizing visitors' CPU power to mine Monero coins in an attempt to gain an extra source of revenue.
Now D-Link has been caught doing the same, although there's high chance that its website has been hacked.
D-Link's official website for Middle East (www.dlinkmea.com) has been found secretly adding a JavaScript-based cryptocurrency miner, according to a blog post published by security firm Seekurity on Tuesday.
Seekurity team was made aware of the issue after Facebook user Ahmed Samir reported that visiting on D-Link Middle East website caused his web browser utilizing a "super high CPU" power usage.
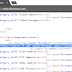
As shown in the screenshot below, a separate domain was loaded using a hidden iFrame for each page view, which included the cryptocurrency mining script.
Five days after Seekurity team reported the issue to D-Link, the company took down the website and redirected it to D-Link USA website (us.dlink.com), without responding to the security firm.
Since the company redirected the whole website to another domain instead of just removing a single line of hidden iFrame code, there are high chances that D-Link has recently been a victim of cyber attack.
Anyways, cryptocurrency mining has become a competitive revenue stream these days, and it is trending among hackers as well.
So, it would be no surprise if hackers compromise popular websites and embed their cryptocurrency miners to harness visitor's system computing power in an attempt to mine digital coins.
Just yesterday it was reported that more than 200 of the top 100,000 websites on the web were found hosting suspicious code from CoinHive and JSEcoin, two popular cryptocurrency mining services, forcing their visitors to run miner code on their computers unknowingly.
If you are using a good antivirus solution, like Malwarebytes and Kaspersky, then you are protected, as most security solutions have already started blocking cryptocurrency mining scripts to prevent their customers from unauthorized mining and extensive CPU usage.
Now D-Link has been caught doing the same, although there's high chance that its website has been hacked.
D-Link's official website for Middle East (www.dlinkmea.com) has been found secretly adding a JavaScript-based cryptocurrency miner, according to a blog post published by security firm Seekurity on Tuesday.
Seekurity team was made aware of the issue after Facebook user Ahmed Samir reported that visiting on D-Link Middle East website caused his web browser utilizing a "super high CPU" power usage.
As shown in the screenshot below, a separate domain was loaded using a hidden iFrame for each page view, which included the cryptocurrency mining script.
Since the company redirected the whole website to another domain instead of just removing a single line of hidden iFrame code, there are high chances that D-Link has recently been a victim of cyber attack.
Anyways, cryptocurrency mining has become a competitive revenue stream these days, and it is trending among hackers as well.
So, it would be no surprise if hackers compromise popular websites and embed their cryptocurrency miners to harness visitor's system computing power in an attempt to mine digital coins.
Just yesterday it was reported that more than 200 of the top 100,000 websites on the web were found hosting suspicious code from CoinHive and JSEcoin, two popular cryptocurrency mining services, forcing their visitors to run miner code on their computers unknowingly.
If you are using a good antivirus solution, like Malwarebytes and Kaspersky, then you are protected, as most security solutions have already started blocking cryptocurrency mining scripts to prevent their customers from unauthorized mining and extensive CPU usage.
Source: feedproxy.google.com
D-Link MEA Site Caught Running Cryptocurrency Mining Script—Or Was It Hacked?
 Reviewed by Anonymous
on
6:52 AM
Rating:
Reviewed by Anonymous
on
6:52 AM
Rating:
 Reviewed by Anonymous
on
6:52 AM
Rating:
Reviewed by Anonymous
on
6:52 AM
Rating:






