Microsoft Issues Emergency Security Updates For Windows 8.1 And Server 2012 R2
Microsoft has issued an emergency out-of-band software update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 systems to patch two new recently disclosed security vulnerabilities.
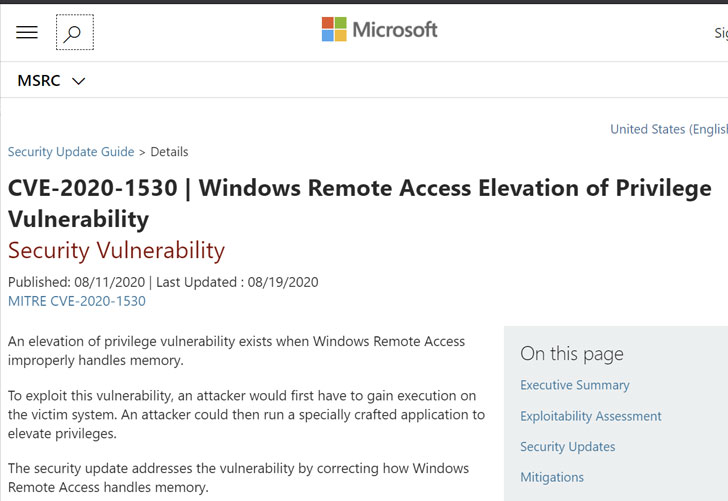
Tracked as CVE-2020-1530 and CVE-2020-1537, both flaws reside in the Remote Access Service (RAS) in a way it manages memory and file operations and could let remote attackers gain elevated privileges after successful exploitation.
In brief, the Remote Access Service functionality of the Windows operating system allows remote clients to connect to the server and access internal resources from anywhere via the Internet.
A patch for both vulnerabilities was first released on August 11 with the batch of August Patch Tuesday updates, but it was for Windows 10, Windows 7, and Windows Server 2008, 2012, 2016, 2019, and Windows Server versions 1903, 1909, and 2004 systems.
A week later, yesterday, on August 19, the company announced that Windows 8.1 and Windows Server 2012 R2 systems are vulnerable to both privilege escalation vulnerabilities and released out-of-band patches.
With a CVSS score of 7.8 out of 10 and 'important' in severity, it is highly recommended for Windows users and sysadmins to install newly available security patches as soon as possible to protect their servers against potential widespread attacks.
Affected users running Windows 8.1, Windows RT 8.1, or Windows Server 2012 R2 can also download and install the standalone packages (KB4578013) from the Microsoft Update Catalogue website.
Besides these two flaws, the recent Patch Tuesday updates notably addressed a total of 120 newly discovered software vulnerabilities, 17 of which have been rated critical, and 2 of them are being exploited in the wild.
Interestingly, as mentioned in our earlier report, if left unpatched, your Windows computer could be hacked even if you:
Tracked as CVE-2020-1530 and CVE-2020-1537, both flaws reside in the Remote Access Service (RAS) in a way it manages memory and file operations and could let remote attackers gain elevated privileges after successful exploitation.
In brief, the Remote Access Service functionality of the Windows operating system allows remote clients to connect to the server and access internal resources from anywhere via the Internet.
A patch for both vulnerabilities was first released on August 11 with the batch of August Patch Tuesday updates, but it was for Windows 10, Windows 7, and Windows Server 2008, 2012, 2016, 2019, and Windows Server versions 1903, 1909, and 2004 systems.
A week later, yesterday, on August 19, the company announced that Windows 8.1 and Windows Server 2012 R2 systems are vulnerable to both privilege escalation vulnerabilities and released out-of-band patches.
With a CVSS score of 7.8 out of 10 and 'important' in severity, it is highly recommended for Windows users and sysadmins to install newly available security patches as soon as possible to protect their servers against potential widespread attacks.
Affected users running Windows 8.1, Windows RT 8.1, or Windows Server 2012 R2 can also download and install the standalone packages (KB4578013) from the Microsoft Update Catalogue website.
Besides these two flaws, the recent Patch Tuesday updates notably addressed a total of 120 newly discovered software vulnerabilities, 17 of which have been rated critical, and 2 of them are being exploited in the wild.
Interestingly, as mentioned in our earlier report, if left unpatched, your Windows computer could be hacked even if you:
- Play a video file,
- Listen to audio,
- Browser a website,
- Edit an HTML page,
- Read a PDF,
- Receive an email message,
- and many other innocent looking activities.
Source: feedproxy.google.com
Microsoft Issues Emergency Security Updates For Windows 8.1 And Server 2012 R2
 Reviewed by Anonymous
on
10:15 AM
Rating:
Reviewed by Anonymous
on
10:15 AM
Rating:
 Reviewed by Anonymous
on
10:15 AM
Rating:
Reviewed by Anonymous
on
10:15 AM
Rating: