Hackers Are Targeting Microsoft Exchange Servers With Ransomware
It didn't take long. Intelligence agencies and cybersecurity researchers had been warning that unpatched Exchange Servers could open the pathway for ransomware infections in the wake of swift escalation of the attacks since last week.
Now it appears that threat actors have caught up.
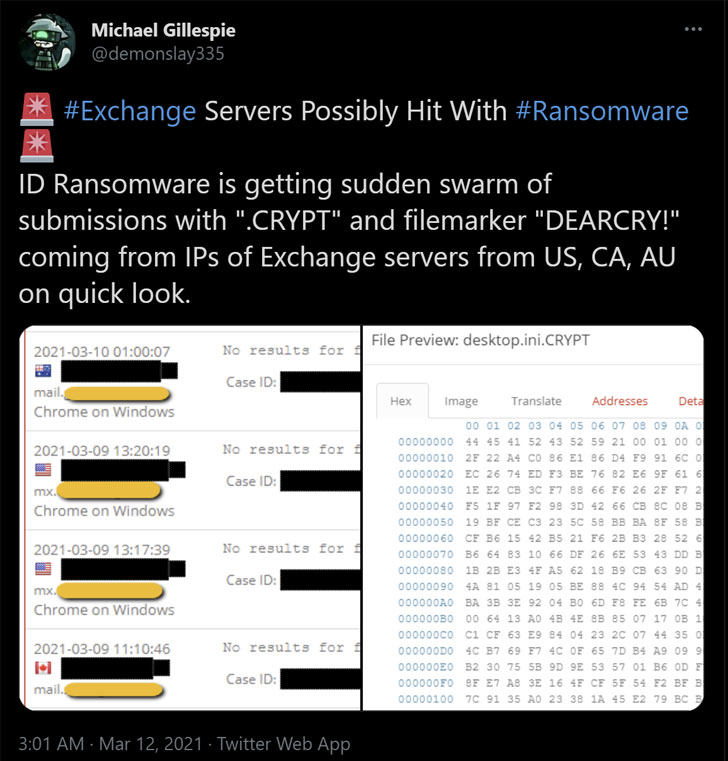
According to the latest reports, cybercriminals are leveraging the heavily exploited ProxyLogon Exchange Server flaws to install a new strain of ransomware called "DearCry."
"Microsoft observed a new family of human operated ransomware attack customers – detected as Ransom:Win32/DoejoCrypt.A," Microsoft researcher Phillip Misner tweeted. "Human operated ransomware attacks are utilizing the Microsoft Exchange vulnerabilities to exploit customers."
In a joint advisory published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), the agencies warned that "adversaries could exploit these vulnerabilities to compromise networks, steal information, encrypt data for ransom, or even execute a destructive attack."
Successful weaponization of the flaws allows an attacker to access victims' Exchange Servers, enabling them to gain persistent system access and control of an enterprise network. With the new ransomware threat, unpatched Servers are not only at risk of potential data theft but also get potentially encrypted, preventing access to an organization's mailboxes.
Meanwhile, as nation-state hackers and cybercriminals pile on to take advantage of the ProxyLogon flaws, a proof-of-concept (PoC) code shared on Microsoft-owned GitHub by a security researcher has been taken down by the company, citing that the exploit is under active attack.
In a statement to Vice, the company said, "In accordance with our Acceptable Use Policies, we disabled the gist following reports that it contains proof of concept code for a recently disclosed vulnerability that is being actively exploited."
The move has also sparked a debate of its own, with researchers arguing that Microsoft is "silencing security researchers" by removing PoCs shared on GitHub.
"This is huge, removing a security researchers code from GitHub against their own product and which has already been patched," TrustedSec's Dave Kennedy said. "It was a PoC, not a working exploit — none of the PoCs have had the RCE. Even if it did, that's not their call on when the appropriate time to release is. It's an issue in their own product, and they are silencing security researchers on that."
This was also echoed by Google Project Zero researcher Tavis Normandy.
"If the policy from the start was no PoC/metasploit/etc — that would suck, but it's their service," Normandy said in a tweet. "Instead they said OK, and now that it's become the standard for security pros to share code, they have elected themselves the arbiters of what is 'responsible.' How convenient."
If anything, the avalanche of attacks should serve as a warning to patch all versions of the Exchange Server as soon as possible, while also take steps to identify signs of indicators of compromise associated with the hacks, given that the attackers were exploiting these zero-day vulnerabilities in the wild for at least two months before Microsoft released the patches on March 2.
We have reached out to Microsoft for more details, and we will update the story if we hear back.
Source: feedproxy.google.com
 Reviewed by Anonymous
on
12:48 AM
Rating:
Reviewed by Anonymous
on
12:48 AM
Rating: