Magecart Hackers Now Hide PHP-Based Backdoor In Website Favicons
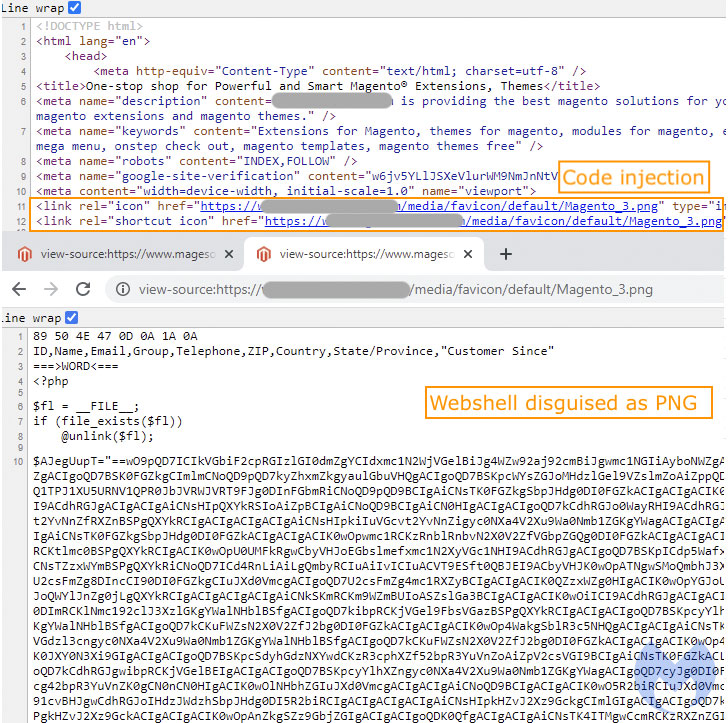
Cybercrime groups are distributing malicious PHP web shells disguised as a favicon to maintain remote access to the compromised servers and inject JavaScript skimmers into online shopping platforms with an aim to steal financial information from their users.
"These web shells known as Smilodon or Megalodon are used to dynamically load JavaScript skimming code via server-side requests into online stores," Malwarebytes Jérôme Segura said in a Thursday write-up. "This technique is interesting as most client-side security tools will not be able to detect or block the skimmer."
Injecting web skimmers on e-commerce websites to steal credit card details is a tried-and-tested modus operandi of Magecart, a consortium of different hacker groups who target online shopping cart systems. Also known as formjacking attacks, the skimmers are typically JavaScript code that the operators stealthily insert into an e-commerce website, often on payment pages, with an intent to capture customers' card details in real-time and transmit it to a remote attacker-controlled server.
While injecting skimmers typically work by making a client-side request to an external JavaScript resource hosted on an attacker-controlled domain when a customer visits the online store in question, the latest attack is a little different in that the skimmer code is introduced into the merchant site dynamically at the server-side.
The PHP-based web shell malware passes off as a favicon ("Magento.png"), with the malware inserted into compromised sites by tampering with the shortcut icon tags in HTML code to point to the fake PNG image file. This web shell, in turn, is configured to retrieve the next-stage payload from an external host, a credit card skimmer that shares similarities with another variant used in Cardbleed attacks last September, suggesting the threat actors modified their toolset following public disclosure.
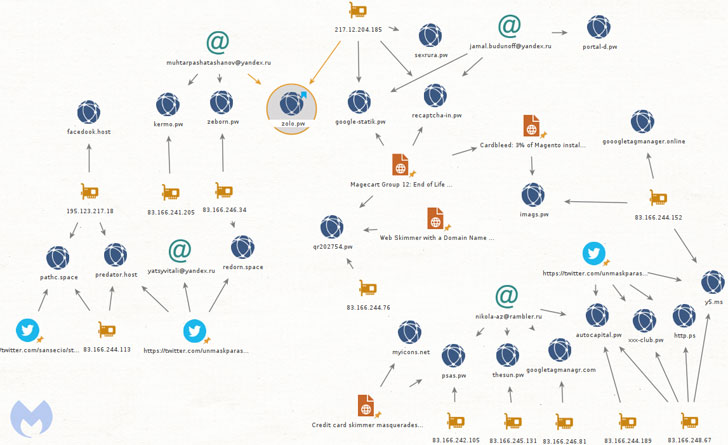
Malwarebytes attributed the latest campaign to Magecart Group 12 based on overlaps in tactics, techniques, and procedures employed, adding "the newest domain name we found (zolo[.]pw) happens to be hosted on the same IP address (217.12.204[.]185) as recaptcha-in[.]pw and google-statik[.]pw, domains previously associated with Magecart Group 12."
Operating with the primary intention of capturing and exfiltrating payment data, Magecart actors have embraced a wide range of attack vectors over the past several months to stay under the radar, avoid detection, and plunder data. From hiding card stealer code inside image metadata and carrying out IDN homograph attacks to plant web skimmers concealed within a website's favicon file to using Google Analytics and Telegram as an exfiltration channel, the cybercrime syndicate has intensified in its efforts to compromise online stores.
Skimming has become so prevalent and lucrative a practice that the Lazarus Group, a collective of state-sponsored hackers affiliated with North Korea, attacked websites that accept cryptocurrency payments with malicious JavaScript sniffers to steal bitcoins and ether in a new campaign called "BTC Changer" that started early last year.
Source: feedproxy.google.com
 Reviewed by Anonymous
on
3:26 AM
Rating:
Reviewed by Anonymous
on
3:26 AM
Rating: