Clop Gang Members Laundered $500 Million In Ransomware Payments
The cybercrime ring that was apprehended last week in connection with Clop (aka Cl0p) ransomware attacks against dozens of companies in the last few months helped launder money totaling $500 million for several malicious actors through a plethora of illegal activities.
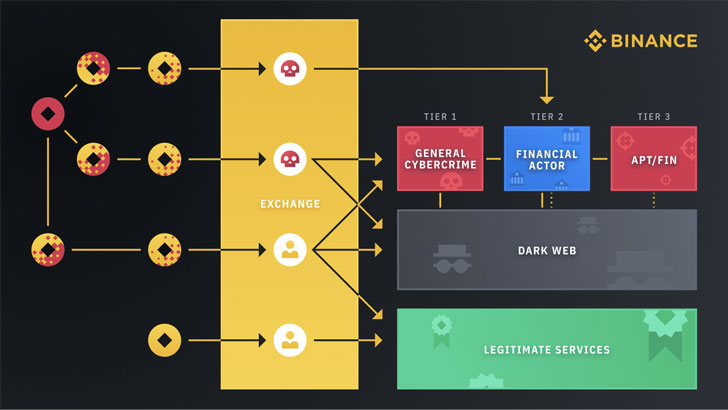
"The group — also known as FANCYCAT — has been running multiple criminal activities: distributing cyber attacks; operating a high-risk exchanger; and laundering money from dark web operations and high-profile cyber attacks such as Cl0p and Petya ransomware," popular cryptocurrency exchange Binance said Thursday.
On June 16, the Ukraine Cyber Police nabbed six individuals in the city of Kyiv, describing the arrests as resulting from an international operation involving law enforcement authorities from Korea, the U.S., and Interpol.
While the bust was seen as a major blow to the operations of the Clop gang, the hackers published earlier this week a fresh batch of confidential employee records stolen from a previously unknown victim on their dark web portal, raising the possibility that the arrested suspects may have been affiliates who play a lesser role in the operations.
Binance's insights into the investigation have now revealed that FANCYCAT was responsible for cashing out and laundering cryptocurrency illicitly obtained by the Clop ransomware cartel by breaching and extorting victims, confirming earlier reports from Intel 471.
Clop is one of several ransomware groups that hack into organizations, launch ransomware that encrypts files and servers, and then demand an extortion payment in return for a digital key needed to unlock access to the systems.
"In a majority of the cases associated with illicit blockchain flows coming onto exchanges, the exchange is not harboring the actual criminal group themselves, but rather being used as a middleman to launder stolen profits," security researchers from Binance said, adding the criminals take advantage of the exchanges' liquidity, diverse digital asset offerings, and well-developed APIs to facilitate cyber attacks.
To counter such nefarious activity from happening, the company said it's implementing custom detection mechanisms to identify and offboard suspicious accounts, adding it's working directly with law enforcement to take down cybercrime groups.
The development comes during a period of intense scrutiny of the risks posed by ransomware, which has ballooned from a lucrative financial crime to a national security threat, grounding critical infrastructure to a halt and causing severe disruptions, necessitating that bitcoin trails be tracked to "follow the money" and fight the spiraling problem.
Source: feedproxy.google.com
 Reviewed by Anonymous
on
11:43 PM
Rating:
Reviewed by Anonymous
on
11:43 PM
Rating: