Another Critical RCE Discovered In Adobe Commerce And Magento Platforms
Adobe on Thursday updated its advisory for an actively exploited zero-day affecting Adobe Commerce and Magento Open Source to patch a newly discovered flaw that could be weaponized to achieve arbitrary code execution.
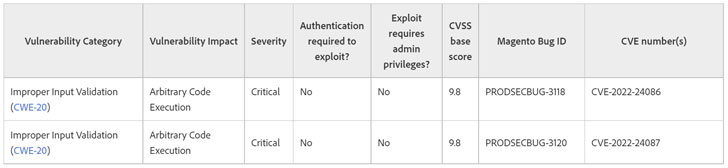
Tracked as CVE-2022-24087, the issue – like CVE-2022-24086 – is rated 9.8 on the CVSS vulnerability scoring system and relates to an "Improper Input Validation" bug that could result in the execution of malicious code.
"We have discovered additional security protections necessary for CVE-2022-24086 and have released an update to address them (CVE-2022-24087)," the company said in a revised bulletin. "Adobe is not aware of any exploits in the wild for the issue addressed in this update (CVE-2022-24087)."
As before, Adobe Commerce and Magento Open Source versions 2.4.3-p1 and earlier and 2.3.7-p2 and earlier are impacted by CVE-2022-24087, but it's worth noting that versions 2.3.0 to 2.3.3 are not vulnerable.
"A new patch have [sic] been published for Magento 2, to mitigate the pre-authenticated remote code execution," security researcher Blaklis, who is credited with discovering the flaw alongside Eboda, tweeted. "If you patched with the first patch, THIS IS NOT SUFFICIENT to be safe. Please update again!"
The patch arrives as cybersecurity firm Positive Technologies disclosed it was able to successfully create an exploit for CVE-2022-24086 to gain remote code execution from an unauthenticated user, making it imperative that customers move quickly to apply the fixes to prevent possible exploitation.
Source: thehackernews.com
 Reviewed by Anonymous
on
7:45 PM
Rating:
Reviewed by Anonymous
on
7:45 PM
Rating: