Dozens Of Security Flaws Discovered In UEFI Firmware Used By Several Vendors
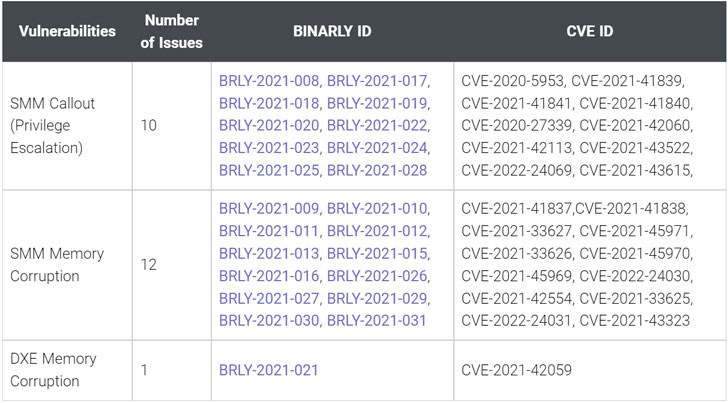
As many as 23 new high severity security vulnerabilities have been disclosed in different implementations of Unified Extensible Firmware Interface (UEFI) firmware used by numerous vendors, including Bull Atos, Fujitsu, HP, Juniper Networks, Lenovo, among others.
The vulnerabilities reside in Insyde Software's InsydeH2O UEFI firmware, according to enterprise firmware security company Binarly, with a majority of the anomalies diagnosed in the System Management Mode (SMM).
UEFI is a software specification that provides a standard programming interface connecting a computer's firmware to its operating system during the booting process. In x86 systems, the UEFI firmware is usually stored in the flash memory chip of the motherboard.
"By exploiting these vulnerabilities, attackers can successfully install malware that survives operating system re-installations and allows the bypass of endpoint security solutions (EDR/AV), Secure Boot, and Virtualization-Based Security isolation," the researchers said.
Successful exploitation of the flaws (CVSS scores: 7.5 - 8.2), could allow a malicious actor to run arbitrary code with SMM permissions, a special-purpose execution mode in x86-based processors that handles power management, hardware configuration, thermal monitoring, and other functions.
"SMM code executes in the highest privilege level and is invisible to the OS, which makes it an attractive target for malicious activity," Microsoft notes in its documentation, adding the SMM attack vector could be abused by a piece of nefarious code to trick another code with higher privileges into performing unauthorized activities.
Worse, the weaknesses can also be chained together to bypass security features and install malware in a manner that survives operating system re-installations and achieve long-term persistence on compromised systems — as observed in the case of MoonBounce — while stealthily creating a communications channel to exfiltrate sensitive data.
Insyde has released firmware patches that address these shortcomings as part of the coordinated disclosure process. But the fact that the software is used in several OEM implementations means it could take a considerable amount of time before the fixes actually trickle down to affected devices.
Source: thehackernews.com
 Reviewed by Anonymous
on
10:55 PM
Rating:
Reviewed by Anonymous
on
10:55 PM
Rating: