Several Malware Families Using Pay-Per-Install Service To Expand Their Targets
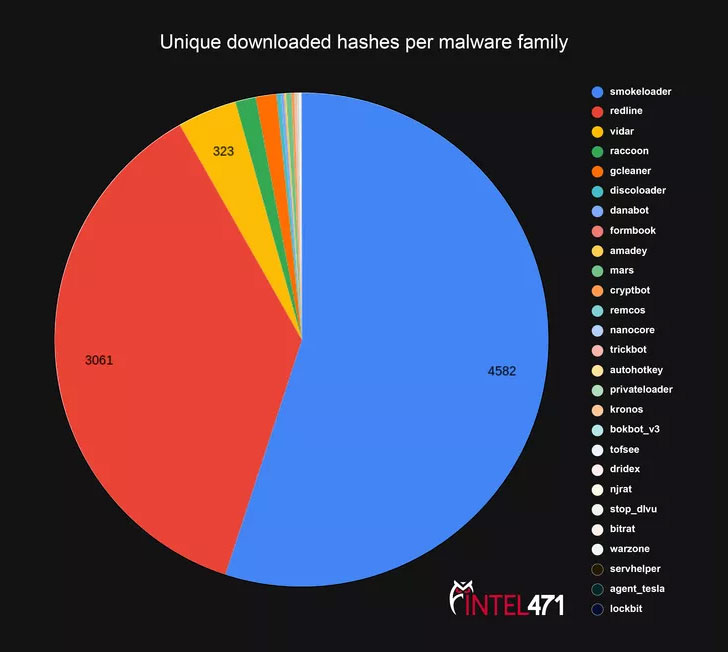
A detailed examination of a Pay-per-install (PPI) malware service called PrivateLoader has revealed its crucial role in the delivery of a variety of malware such as SmokeLoader, RedLine Stealer, Vidar, Raccoon, and GCleaner since at least May 2021.
Loaders are malicious programs used for loading additional executables onto the infected machine. With PPI malware services such as PrivateLoader, malware operators pay the service owners to get their payloads "installed" based on the targets provided.
"The accessibility and moderate costs allow malware operators to leverage these services as another weapon for rapid, bulk and geo-targeted malware infections," cybersecurity firm Intel 471 said in a new report shared with The Hacker News.
PrivateLoader, written in the C++ programming language, is designed to retrieve URLs for the malicious payloads to be deployed on the infected host, with the distribution primarily relying on a network of bait websites that have been rigged to appear prominently in search results via search engine optimization (SEO) poisoning methods targeting users looking for pirated software.
The administrative panel used by the PPI service offers a wealth of functions, including adding new users, configuring a link to the payload to be installed, modifying geolocation targeting based on the campaign, and even encrypting the load file.
Other common payload families pushed by PrivateLoader include a mix of remote access trojans, banking malware, and ransomware like DanaBot, Formbook (aka XLoader), CryptBot, Remcos, NanoCore, TrickBot, Kronos, Dridex, NjRAT, BitRAT, Agent Tesla, and LockBit.
"PPI services have been a pillar of cybercrime for decades," the researchers said. "Just like the wider population, criminals are going to flock to software that provides them a wide array of options to easily achieve their goals."
Source: thehackernews.com
 Reviewed by Anonymous
on
4:53 AM
Rating:
Reviewed by Anonymous
on
4:53 AM
Rating: