Chinese APT Hackers Targeting Betting Companies In Southeast Asia
A Chinese-speaking advanced persistent threat (APT) has been linked to a new campaign targeting gambling-related companies in South East Asia, particularly Taiwan, the Philippines, and Hong Kong.
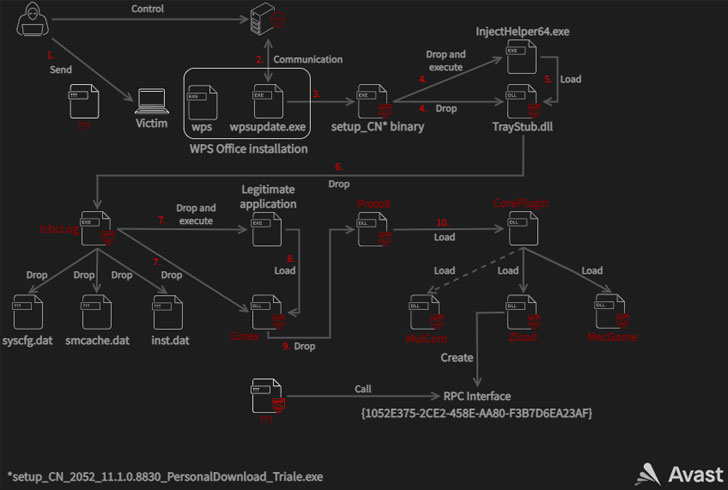
Cybersecurity firm Avast dubbed the campaign Operation Dragon Castling, describing its malware arsenal as a "robust and modular toolset." The ultimate motives of the threat actor are not immediately discernible as yet nor has it been linked to a known hacking group.
While multiple initial access avenues were employed during the course of the campaign, one of the attack vectors involved leveraging a previously unknown remote code execution flaw in the WPS Office suite (CVE-2022-24934) to backdoor its targets. The issue has since been addressed by Kingsoft Office, the developers of the office software.
In the case observed by the Czech security firm, the vulnerability was used to drop a malicious binary from a fake update server with the domain update.wps[.]cn that triggers a multi-stage infection chain that leads to the deployment of intermediate payloads the allows for privilege escalation before ultimately dropping the Proto8 module.
"The core module is a single DLL that is responsible for setting up the malware's working directory, loading configuration files, updating its code, loading plugins, beaconing to [command-and-control] servers and waiting for commands," Avast researchers Luigino Camastra, Igor Morgenstern, Jan Holman said.
Proto8's plugin-based system used to extend its functionality enables the malware to achieve persistence, bypass user account control (UAC) mechanisms, create new backdoor accounts, and even execute arbitrary commands on the infected system.
Source: thehackernews.com
 Reviewed by Anonymous
on
6:22 AM
Rating:
Reviewed by Anonymous
on
6:22 AM
Rating: