TeaBot Android Banking Malware Spreads Again Through Google Play Store Apps
An Android banking trojan designed to steal credentials and SMS messages has been observed sneaking past Google Play Store protections to target users of more than 400 banking and financial apps from Russia, China, and the U.S.
"TeaBot RAT capabilities are achieved via the device screen's live streaming (requested on-demand) plus the abuse of Accessibility Services for remote interaction and key-logging," Cleafy researchers said in a report. "This enables Threat Actors (TAs) to perform ATO (Account Takeover) directly from the compromised phone, also known as 'On-device fraud.'"
Also known by the name Anatsa, TeaBot first emerged in May 2021, camouflaging its malicious functions by posing as seemingly innocuous PDF document and QR code scanner apps that are distributed via the official Google Play Store instead of third-party apps stores or via fraudulent websites.
These apps, also known as dropper applications, act as a conduit to deliver a second-stage payload that retrieves the malware strain to take control of the infected devices. In November 2021, Dutch security firm ThreatFabric disclosed that it had identified six Anatsa droppers on the Play Store since June last year.
Then earlier this January, Bitdefender researchers identified TeaBot lurking in the official Android app marketplace as a "QR Code Reader - Scanner App," gaining more than 100,000 downloads within a span of a month before it was taken down.
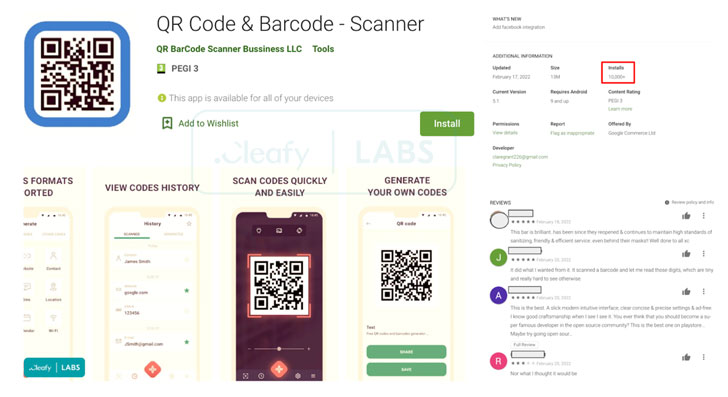
The latest version of TeaBot dropper spotted by Cleafy on February 21, 2022, is also a QR code reader app named "QR Code & Barcode - Scanner" which has been downloaded roughly 10,000 times from the Play Store.
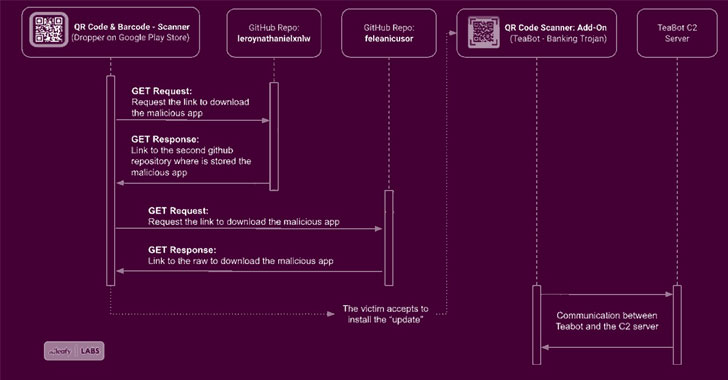
Once installed the modus operandi is the same: prompt users to accept a fake add-on update, which, in turn, leads to the installation of a second app hosted on GitHub that actually contains the TeaBot malware. It's, however, worth noting that users need to allow installs from unknown sources for this attack chain to be successful.
The last phase of the infection involves the banking trojan seeking Accessibility Services permissions to capture sensitive information like login credentials and two-factor authentication codes with the goal of taking over the accounts to carry out on-device fraud.
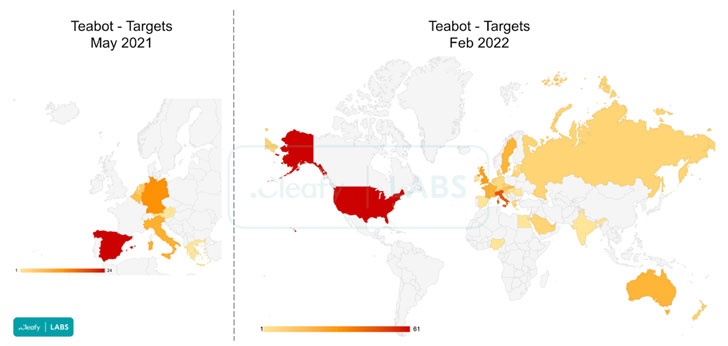
"In less than a year, the number of applications targeted by TeaBot have grown more than 500%, going from 60 targets to over 400," the researchers said, adding the malware now strikes several apps related to personal banking, insurance, crypto wallets, and crypto exchanges.
Source: thehackernews.com
 Reviewed by Anonymous
on
10:28 PM
Rating:
Reviewed by Anonymous
on
10:28 PM
Rating: