Experts Shed Light On BlackGuard Infostealer Malware Sold On Russian Hacking Forums
A previously undocumented "sophisticated" information-stealing malware named BlackGuard is being advertised for sale on Russian underground forums for a monthly subscription of $200.
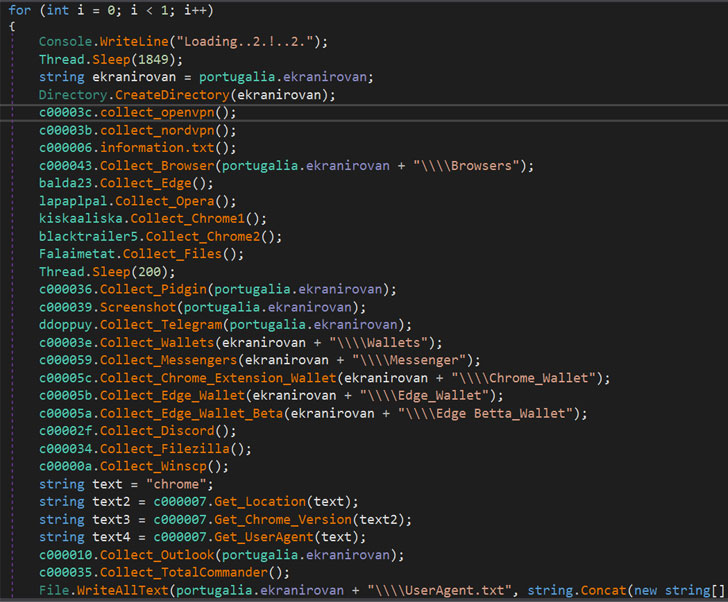
"BlackGuard has the capability to steal all types of information related to Crypto wallets, VPN, Messengers, FTP credentials, saved browser credentials, and email clients," Zscaler ThreatLabz researchers Mitesh Wani and Kaivalya Khursale said in a report published last week.
Also sold for a lifetime price of $700, BlackGuard is designed as a .NET-based malware that's actively under development, boasting of a number of anti-analysis, anti-debugging, and anti-evasion features that allows it to kill processes related to antivirus engines and bypass string-based detection.
What's more, it checks the IP address of the infected devices by sending a request to the domain "https://ipwhois[.]app/xml/," and exit itself if the country is one among the Commonwealth of Independent States (CIS).
BlackGuard's extensive functionality means it can amass information stored in browsers, such as passwords, cookies, autofill data, browsing history, 17 different cold cryptocurrency wallets, and as many as six messaging apps, including Telegram, Signal, Tox, Element, Pidgin, and Discord.
In addition, the malware targets 21 crypto wallet extensions installed in Chrome and Edge browsers, and three VPN apps NordVPN, OpenVPN, and ProtonVPN, the results of which are subsequently compressed into a ZIP archive and exfiltrated to a remote server.
The findings come as Morphisec disclosed details of another infostealer family called Mars that's been observed leveraging fraudulent Google Ads for well-known software like OpenOffice to distribute the malware.
"While applications of BlackGuard are not as broad as other stealers, BlackGuard is a growing threat as it continues to be improved and is developing a strong reputation in the underground community," the researchers said.
Source: thehackernews.com
 Reviewed by Anonymous
on
2:59 AM
Rating:
Reviewed by Anonymous
on
2:59 AM
Rating: