Watch Out! Hackers Begin Exploiting Recent Zyxel Firewalls RCE Vulnerability
 |
| Image source: z3r00t |
The U.S. Cybersecurity and Infrastructure Security Agency on Monday added two security flaws, including the recently disclosed remote code execution bug affecting Zyxel firewalls, to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation.
Tracked as CVE-2022-30525, the vulnerability is rated 9.8 for severity and relates to a command injection flaw in select versions of the Zyxel firewall that could enable an unauthenticated adversary to execute arbitrary commands on the underlying operating system.
Impacted devices include -
- USG FLEX 100, 100W, 200, 500, 700
- USG20-VPN, USG20W-VPN
- ATP 100, 200, 500, 700, 800, and
- VPN series
The issue, for which patches were released by the Taiwanese firm in late April (ZLD V5.30), became public knowledge on May 12 following a coordinated disclosure process with Rapid7.
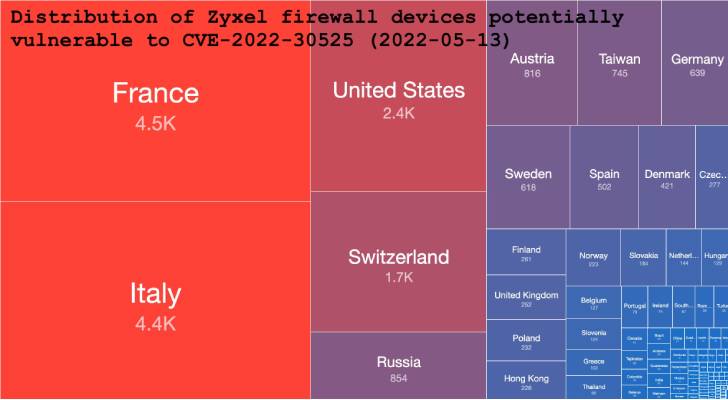 |
| Source: Shadowserver |
Merely a day later, the Shadowserver Foundation said it began detecting exploitation attempts, with most of the vulnerable appliances located in France, Italy, the U.S., Switzerland, and Russia.
Also added by CISA to the catalog is CVE-2022-22947, another code injection vulnerability in Spring Cloud Gateway that could be exploited to allow arbitrary remote execution on a remote host by means of a specially crafted request.
The vulnerability is rated 10 out of 10 on the CVSS vulnerability scoring system and has since been addressed in Spring Cloud Gateway versions 3.1.1 or later and 3.0.7 or later as of March 2022.
Source: thehackernews.com
 Reviewed by Zion3R
on
8:28 PM
Rating:
Reviewed by Zion3R
on
8:28 PM
Rating:






