A Decade-Long Chinese Espionage Campaign Targets Southeast Asia And Australia
A previously undocumented Chinese-speaking advanced persistent threat (APT) actor dubbed Aoqin Dragon has been linked to a string of espionage-oriented attacks aimed at government, education, and telecom entities chiefly in Southeast Asia and Australia dating as far back as 2013.
"Aoqin Dragon seeks initial access primarily through document exploits and the use of fake removable devices," SentinelOne researcher Joey Chen said in a report shared with The Hacker News. "Other techniques the attacker has been observed using include DLL hijacking, Themida-packed files, and DNS tunneling to evade post-compromise detection."
The group is said to have some level of association with another threat actor known as Naikon (aka Override Panda), with campaigns primarily directed against targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.
Infections chains mounted by Aoqin Dragon have banked on Asia-Pacific political affairs and pornographic-themed document lures as well as USB shortcut techniques to trigger the deployment of one of two backdoors: Mongall and a modified version of the open-source Heyoka project.
This involved leveraging old and unpatched security vulnerabilities (CVE-2012-0158 and CVE-2010-3333), with the decoy documents enticing targets into opening the files. Over the years, the threat actor also employed executable droppers masquerading as antivirus software to deploy the implant and connect to a remote server.
"Although executable files with fake file icons have been in use by a variety of actors, it remains an effective tool especially for APT targets," Chen explained. "Combined with 'interesting' email content and a catchy file name, users can be socially engineered into clicking on the file."
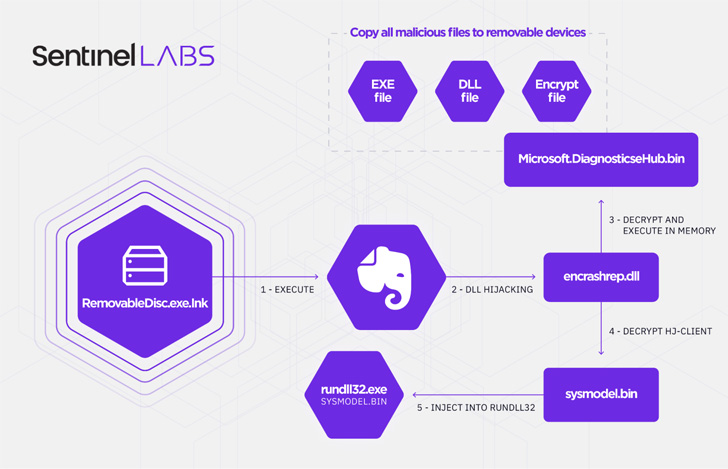
That said, Aoqin Dragon's newest initial access vector of choice since 2018 has been its use of a fake removable device shortcut file (.LNK), which , when clicked, runs an executable ("RemovableDisc.exe") that sports the icon for the popular note-taking app Evernote but is engineered to function as a loader for two different payloads.
One of the components in the infection chain is a spreader that copies all malicious files to other removable devices and the second module is an encrypted backdoor that injects itself into rundll32's memory, a native Windows process used to load and run DLL files.
Known to be used since at least 2013, Mongall ("HJ-client.dll") is described as a not-so "particularly feature rich" implant but one that packs enough features to create a remote shell and upload and download arbitrary files to and from the attacker-control server.
Also used by the adversary is a reworked variant of Heyoka ("srvdll.dll"), a proof-of-concept (PoC) exfiltration tool "which uses spoofed DNS requests to create a bidirectional tunnel." The modified Heyoka backdoor is more powerful, equipped with capabilities to create, delete, and search for files, create and terminate processes, and gather process information on a compromised host.
"Aoqin Dragon is an active cyber espionage group that has been operating for nearly a decade," Chen said, adding, "it is likely they will also continue to advance their tradecraft, finding new methods of evading detection and stay longer in their target network."
Source: thehackernews.com
 Reviewed by Zion3R
on
4:01 AM
Rating:
Reviewed by Zion3R
on
4:01 AM
Rating: