Avoiding Death By A Thousand Scripts: Using Automated Content Security Policies
Businesses know they need to secure their client-side scripts. Content security policies (CSPs) are a great way to do that. But CSPs are cumbersome. One mistake and you have a potentially significant client-side security gap. Finding those gaps means long and tedious hours (or days) in manual code reviews through thousands of lines of script on your web applications. Automated content security policies can help streamline the code review process by first identifying all first- and third-party scripts and the assets they access, and then generating an appropriate content security policy to help better secure the client-side attack surface.
There are few developers or AppSec professionals who claim to enjoy deploying CSPs. First, the CSP has to work for the specific web application. Then the team needs to make sure it provides the appropriate level of protection. The CSP also can't conflict with any existing widgets or plugins (or the decision must be made to not deploy the CSP or deactivate those plugins, which can cause problems in other areas, such as customer engagement, marketing, and sales).
And then, when a CSP fails, there is the dreaded audit to determine the why and where.
The CSP-audit-avoidance problem (aka avoiding manual code reviews or death by a thousand scripts) is fairly common. Today, client-side web applications contain thousands of scripts, assembled from multiple open-source libraries or other third- and fourth-party repositories. Few development or security teams take the time to maintain a detailed record of all the scripts used in web application assembly, including their functions, their sources, and whether they've been updated or patched to address any known security issues.
Even when teams do identify all third-party script sources, that's no guarantee that the scripts are safe. Ongoing issues still surface with package managers containing obfuscated and malicious JavaScript used to harvest sensitive information from websites and web applications. In a recent example, researchers discovered that malicious packages had been downloaded 27,000 times by unsuspecting developers.
Unfortunately, the CSP-audit-avoidance problem expands an already significant client-side attack surface.
The problems with CSPs have nothing to do with their value. CSPs are great at providing violation reporting and policy optimization and help uncover vulnerable scripts that lead to JavaScript injection attacks, cross-site scripting (XSS), and skimming attacks, like Magecart. Manual content security policies are just a pain to manage, which means developers may avoid critical CSP processes, leading to increased security risk.
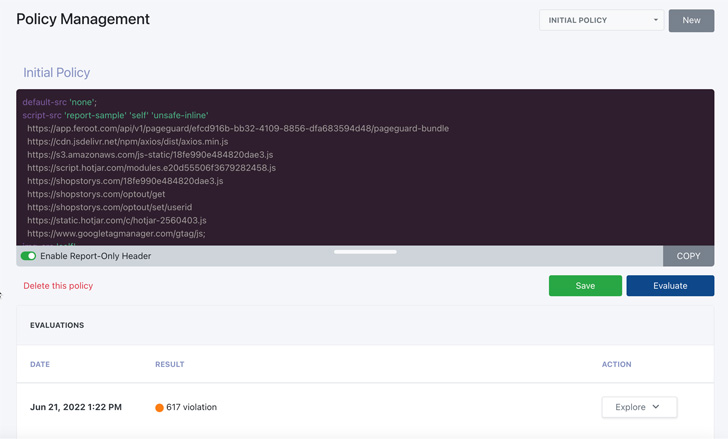
Automated content security policies help manage CSPs to better protect the client-side attack surface and remove the risk associated with manual CSP oversight. By identifying all first- and third-party scripts, digital assets, and the data these assets access, businesses can streamline the CSP creation and management process, and improve overall client-side security. Automated CSPs are managed at the domain level for better reporting and version control.
Automated CSPs work by crawling a website or web application and initiating synthetic users to assess how scripts are operating on the web application and what type of data the script may be accessing. The system then generates the CSP to align it with the security needs of the website or web application. Automated CSPs also work within the actual production environment, to emulate policies for quick testing (and avoid constant CSP deployment in a development environment) and focus on bringing policy violations as close to zero as possible.
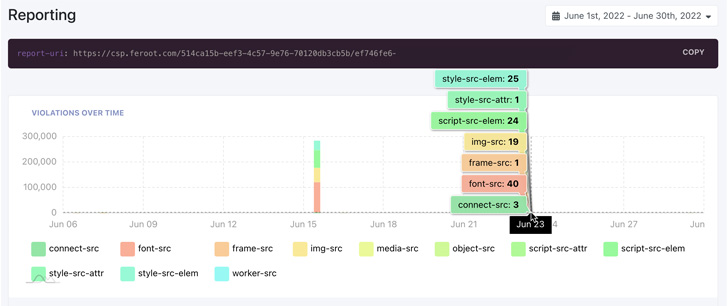
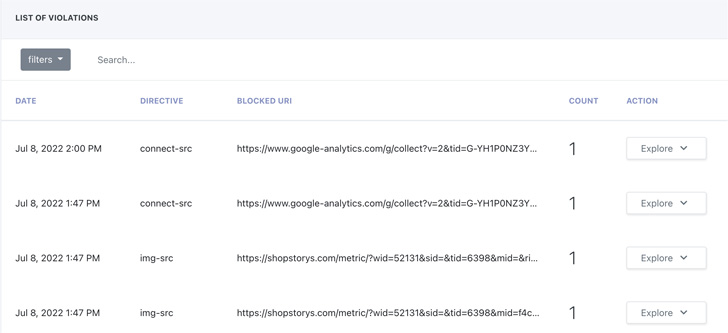
Additional features of an automated CSP include creating new policies after a detected violation to enable fast updates and address current security threats and ingesting log data into security incident and event management (SIEM) and other log-based data collection systems for integration into current security practices and workflows.
With violation reporting fully integrated, an automated CSP solution complements current security processes and workflows. It also provides critical support for regulatory and compliance standards like PCI DSS 4.0, HIPAA, and others.
Feroot Security offers DomainGuard, a purpose-built, automated CSP that helps organizations manage their client-side attack surface by simplifying the content security policy management process. DomainGuard integrates violation reporting with existing security tools to complement current security processes and workflows and significantly reduce the time it takes to create and manage CSPs across teams, websites, and web applications.
Source: thehackernews.com
 Reviewed by Zion3R
on
4:30 AM
Rating:
Reviewed by Zion3R
on
4:30 AM
Rating: