Bitter APT Hackers Continue To Target Bangladesh Military Entities
Military entities located in Bangladesh continue to be at the receiving end of sustained cyberattacks by an advanced persistent threat tracked as Bitter.
"Through malicious document files and intermediate malware stages the threat actors conduct espionage by deploying Remote Access Trojans," cybersecurity firm SECUINFRA said in a new write-up published on July 5.
The findings from the Berlin-headquartered company build on a previous report from Cisco Talos in May, which disclosed the group's expansion in targeting to strike Bangladeshi government organizations with a backdoor called ZxxZ.
Bitter, also tracked under the codenames APT-C-08 and T-APT-17, is said to be active since at least late 2013 and has a track record of targeting China, Pakistan, and Saudi Arabia using different tools such as BitterRAT and ArtraDownloader.
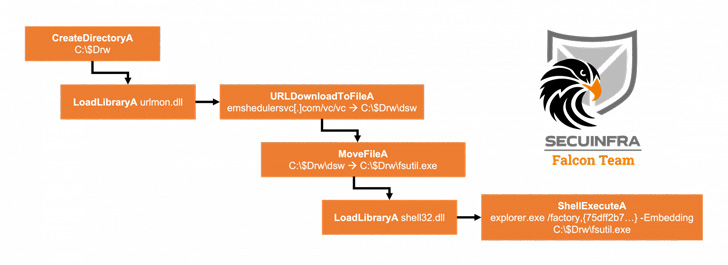
The latest attack chain detailed by SECUINFRA is believed to have been conducted in mid-May 2022, originating with a weaponized Excel document likely distributed by means of a spear-phishing email that, when opened, exploits the Microsoft Equation Editor exploit (CVE-2018-0798) to drop the next-stage binary from a remote server.
ZxxZ (or MuuyDownloader by the Qi-Anxin Threat Intelligence Center), as the downloaded payload is called, is implemented in Visual C++ and functions as a second-stage implant that allows the adversary to deploy additional malware.
The most notable change in the malware is that it has dropped using "ZxxZ" as the separator used when sending information back to the command-and-control (C2) server in favor of an underscore, suggesting that the group is actively making modifications to its source code to stay under the radar.
Also put to use by the threat actor in its campaigns is a backdoor dubbed Almond RAT, a .NET-based RAT that first came to light in May 2022 and offers basic data gathering functionality and the ability to execute arbitrary commands. Additionally, the implant employs obfuscation and string encryption techniques to evade detection and to hinder analysis.
"Almond RATs main purposes seem to be file system discovery, data exfiltration and a way to load more tools/establish persistence," the researchers said. "The design of the tools seems to be laid out in a way that it can be quickly modified and adapted to the current attack scenario."
Source: thehackernews.com
 Reviewed by Zion3R
on
3:00 AM
Rating:
Reviewed by Zion3R
on
3:00 AM
Rating: