Hackers Aid Protests Against Iranian Government With Proxies, Leaks And Hacks
Several hacktivist groups are using Telegram and other tools to aid anti-government protests in Iran to bypass regime censorship restrictions amid ongoing unrest in the country following the death of Mahsa Amini in custody.
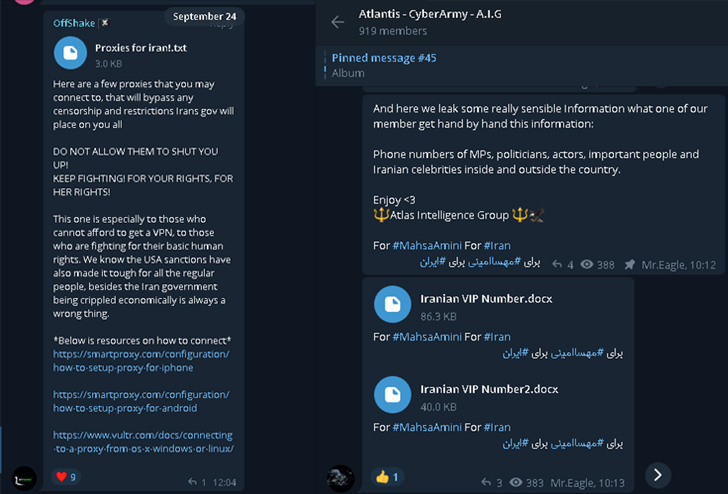
"Key activities are data leaking and selling, including officials' phone numbers and emails, and maps of sensitive locations," Israeli cybersecurity firm Check Point said in a new report.
The company said it has also witnessed sharing of proxies and open VPN servers to get around censorship and reports on the internet status in the country, with one group helping the anti-government demonstrators access social media sites.
Chief among them is a Telegram channel called Official Atlas Intelligence Group (AIG) that's primarily focused on publishing data associated with government officials as well as maps of prominent locations.
Calling itself the "CyberArmy," the group is said to have commenced its operations in May and has also advertised a wide range of services in the past, such as data leaks, DDoS attacks, and remote access to organizations. It's also known to voluntarily hunt and dox pedophiles.
According to Cyberint, the cyber mercenary actor also claims to have "connections with people in several law enforcement entities in Europe who can deliver sensitive information about certain individuals exclusively."
A second group of interest is ARVIN, which consists of about 5,000 members and shares news reports about the ongoing protests along with providing a list of Open VPN servers to circumvent internet blockades.
RedBlue™, a 4,000-member group on Telegram, has also pitched in with similar efforts, in addition to sharing hacking conversations and guides.
Privacy-focused messaging app Signal, for its part, has reached out to its community to set up a proxy that will help people in the country use the service on Android.
Source: thehackernews.com
 Reviewed by Zion3R
on
3:52 AM
Rating:
Reviewed by Zion3R
on
3:52 AM
Rating: