Iranian Hackers Target High-Value Targets In Nuclear Security And Genomic Research
Hackers tied to the Iranian government have been targeting individuals specializing in Middle Eastern affairs, nuclear security and genome research as part of a new social engineering campaign designed to hunt for sensitive information.
Enterprise security firm attributed the targeted attacks to a threat actor named TA453, which broadly overlaps with cyber activities monitored under the monikers APT42, Charming Kitten, and Phosphorus.
It all starts with a phishing email impersonating legitimate individuals at Western foreign policy research organizations that's ultimately designed to gather intelligence on behalf of Iran's Islamic Revolutionary Guard Corps (IRGC).
Spoofed personas include people from Pew Research Center, the Foreign Policy Research Institute (FRPI), the U.K.'s Chatham House, and the scientific journal Nature. The technique is said to have been deployed in mid-June 2022.
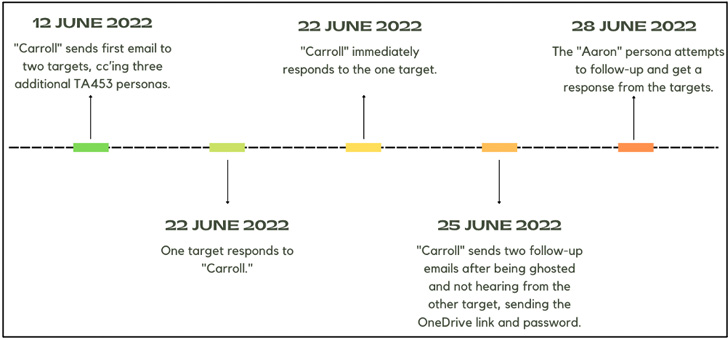
What's different from other phishing attacks is the use of a tactic Proofpoint calls Multi-Persona Impersonation (MPI), wherein the threat actor employs not one but several actor-controlled personas in the same email conversation to bolster the chances of success.
The idea is to "leverage the psychology principle of social proof" and increase the authenticity of the threat actor's correspondence so as to make the target buy into the scheme, a tactic that demonstrates the adversary's continued ability to step up its game.
"This is an intriguing technique because it requires more resources to be used per target – potentially burning more personas – and a coordinated approach among the various personalities in use by TA453," Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said in a statement.
Once the initial email elicits a response from the target, the persona then sends a follow-up message containing a malicious OneDrive link that downloads a Microsoft Office document, one of which purportedly alludes to a clash between Russia and the U.S.
This document subsequently uses a technique called remote template injection to download Korg, a template consisting of three macros that are capable of gathering usernames, a list of running processes, and the victims' public IP addresses.
Besides the exfiltration of the beaconing information, no other post-exploitation actions have been observed. The "abnormal" lack of code execution and command-and-control behavior has led to an assessment that the compromised users may be subjected to further attacks based on the installed software.
This is not the first time the threat actor has undertaken impersonation campaigns. In July 2021, Proofpoint revealed a phishing operation dubbed SpoofedScholars that targeted individuals focused on Middle East affairs in the U.S. and the U.K. under the guise of scholars with the University of London's School of Oriental and African Studies (SOAS).
Then in July 2022, the cybersecurity company uncovered attempts on the part of TA453 to masquerade as journalists to lure academics and policy experts into clicking on malicious links that redirect the targets to credential harvesting domains.
The disclosure comes amid a flurry of Iranian-linked cyber activity. Last week, Microsoft took the wraps off a string of ransomware attacks mounted by a Phosphorus subgroup dubbed DEV-0270 using living-off-the-land binaries such as BitLocker.
Additionally, cybersecurity firm Mandiant, which is now officially part of Google Cloud, detailed the activities of an Iranian espionage actor codenamed APT42 that has been linked to over 30 operations since 2015.
To top it all, the Treasury Department announced sanctions against Iran's Ministry of Intelligence and Security (MOIS) and its Minister of Intelligence, Esmaeil Khatib, in response to "cyber-enabled activities against the United States and its allies."
Albania, which has severed diplomatic relations with Iran after blaming it for a series of cyber offensives since July, pointed fingers at the "same aggressors" over the weekend for conducting another attack on a government system used to track border crossings.
"State-aligned threat actors are some of the best at crafting well thought-out social engineering campaigns to reach their intended victims," DeGrippo said.
"Researchers involved in international security, particularly those specializing in Middle Eastern studies or nuclear security, should maintain a heightened sense of awareness when receiving unsolicited emails."
Source: thehackernews.com
 Reviewed by Zion3R
on
2:54 AM
Rating:
Reviewed by Zion3R
on
2:54 AM
Rating: