New Prestige Ransomware Targeting Polish And Ukrainian Organizations
A new ransomware campaign targeted the transportation and logistics sectors in Ukraine and Poland on October 11 with a previously unknown payload dubbed Prestige.
"The activity shares victimology with recent Russian state-aligned activity, specifically on affected geographies and countries, and overlaps with previous victims of the FoxBlade malware (also known as HermeticWiper)," the Microsoft Threat Intelligence Center (MSTIC) said.
The tech giant remarked the intrusions occurred within an hour of each other across all victims, attributing the infections to an unnamed cluster called DEV-0960. It did not disclose the scale of the attacks, but stated it's notifying all affected customers.
The campaign is also believed to be distinct from other recent destructive attacks that have involved the use of HermeticWiper and CaddyWiper, the latter of which is launched by a malware loader called ArguePatch (aka AprilAxe).
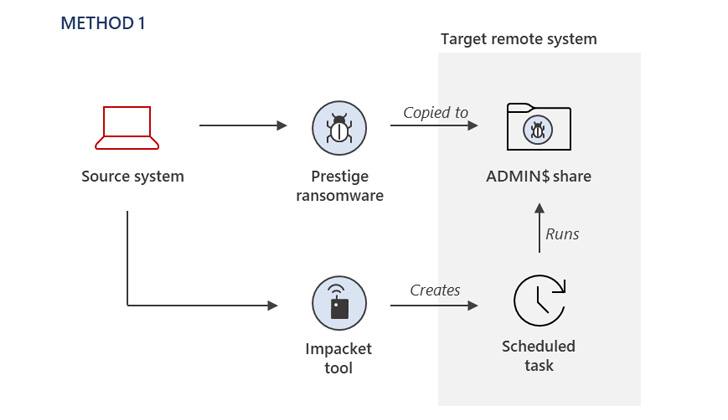
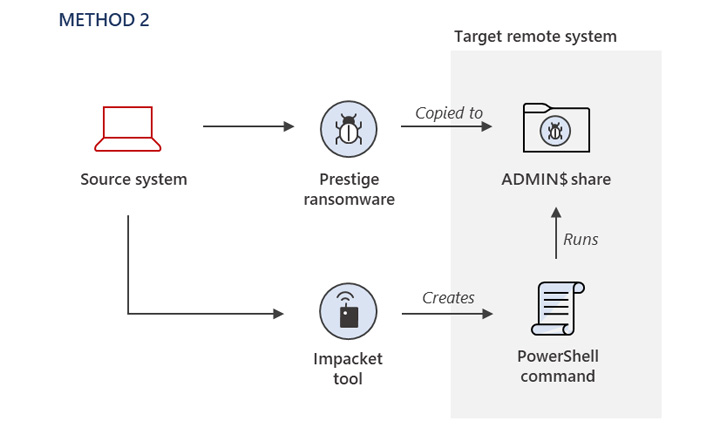
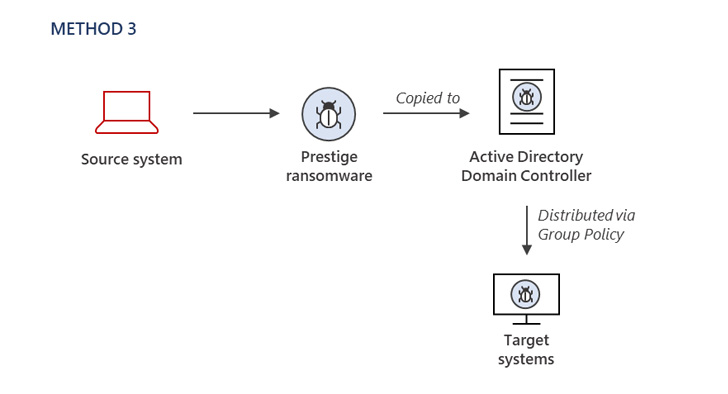
The method of initial access remains unknown, with Microsoft noting that the threat actor had already obtained privileged access to the compromised environment to deploy the ransomware using three different methods.
In a related development, Fortinet FortiGuard Labs took the wraps off a multi-stage attack chain that leverages a weaponized Microsoft Excel document, which masquerades as a spreadsheet for generating salaries for Ukrainian military personnel to drop Cobalt Strike Beacon.
"The threat landscape in Ukraine continues to evolve, and wipers and destructive attacks have been a consistent theme," Redmond noted. "Ransomware and wiper attacks rely on many of the same security weaknesses to succeed."
The findings come amid an explosion of relatively new ransomware strains that have been gaining traction on the threat landscape, including that of Bisamware, Chile Locker, Royal, and Ransom Cartel, over the past few months.
Ransom Cartel, which surfaced in mid-December 2021, is also notable for sharing technical overlaps with REvil ransomware, which shut shop in October 2021 following immense law enforcement scrutiny into its operations after a string of high-profile attacks on JBS and Kaseya.
It's suspected that "Ransom Cartel operators had access to earlier versions of REvil ransomware source code," Palo Alto Networks Unit 42 observed on October 14, stating that "there was a relationship between the groups at some point, though it may not have been recent."
REvil, earlier this January, suffered further setback when Russian authorities arrested multiple members, but there are indications that the notorious cybercrime cartel may have staged a return in some form.
Cybersecurity firm Trellix, in late September, also revealed how a "disgruntled internal source" from the group shared details about the adversary's Tactics, Techniques and Procedures (TTPs), lending a crucial insight into the "relationships and inner workings of REvil and its members."
It's not just REvil that's back on the ransomware radar. HP Wolf Security last week said it isolated a Magniber campaign that has been found targeting Windows home users with fake security updates which employ a JavaScript file to proliferate the file-encrypting malware.
"The attackers used clever techniques to evade protection and detection mechanisms," malware analyst Patrick Schläpfer pointed out. "Most of the infection chain is 'fileless,' meaning the malware only resides in memory, reducing the chances of it being detected."
Source: thehackernews.com
 Reviewed by Zion3R
on
5:58 AM
Rating:
Reviewed by Zion3R
on
5:58 AM
Rating: