Italian Users Warned Of Malware Attack Targeting Sensitive Information
A new malware campaign has been observed targeting Italy with phishing emails designed to deploy an information stealer on compromised Windows systems.
"The info-stealer malware steals sensitive information like system info, crypto wallet and browser histories, cookies, and credentials of crypto wallets from victim machines," Uptycs security researcher Karthickkumar Kathiresan said in a report.
Details of the campaign were first disclosed by Milan-based IT services firm SI.net last month.
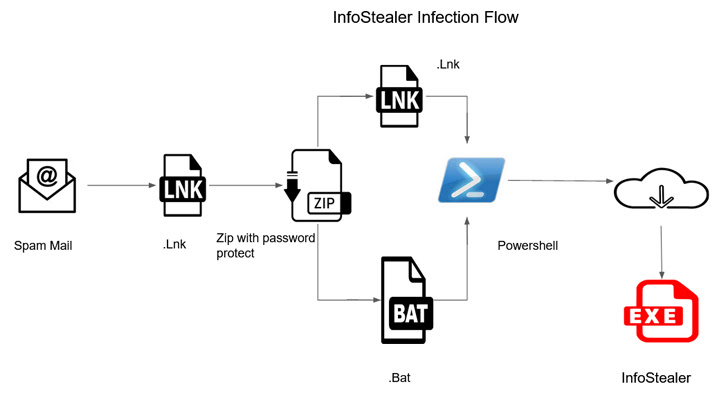
The multi-stage infection sequence commences with an invoice-themed phishing email containing a link that, when clicked, downloads a password-protected ZIP archive file, which harbors two files: A shortcut (.LNK) file and a batch (.BAT) file.
Irrespective of which file is launched, the attack chain remains the same, as opening the shortcut file fetches the same batch script designed to install the information stealer payload from a GitHub repository. This is achieved by leveraging a legitimate PowerShell binary that's also retrieved from GitHub.
Once installed, the C#-based malware gathers system metadata, and information from dozens of web browsers (e.g., cookies, bookmarks, credit cards, downloads, and credentials), as well as several cryptocurrency wallets, all of which is transmitted to an actor-controlled domain.
To mitigate such attacks, organizations are recommended to implement "tight security controls and multi-layered visibility and security solutions to identify and detect malware."
Source: thehackernews.com
 Reviewed by Zion3R
on
6:36 AM
Rating:
Reviewed by Zion3R
on
6:36 AM
Rating: