International Law Enforcement Takes Down Infamous NetWire Cross-Platform RAT
A coordinated international law enforcement exercise has taken down the online infrastructure associated with a cross-platform remote access trojan (RAT) known as NetWire.
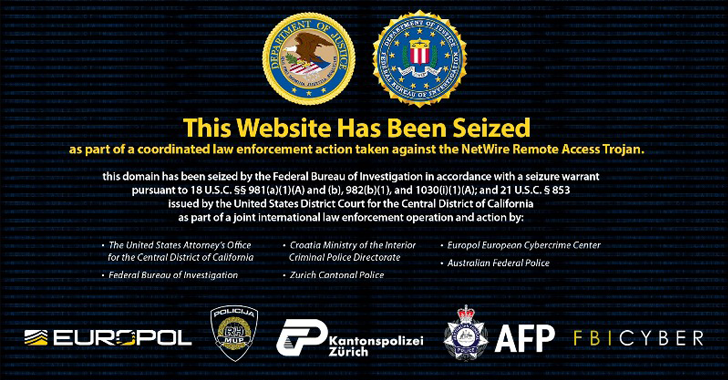
Coinciding with the seizure of the sales website www.worldwiredlabs[.]com, a Croatian national who is suspected to be the website's administrator has been arrested. While the suspect's name was not released, investigative journalist Brian Krebs identified Mario Zanko as the owner of the domain.
"NetWire is a licensed commodity RAT offered in underground forums to non-technical users to carry out their own criminal activities," Europol's European Cybercrime Center (EC3) said in a tweet.
Advertised since at least 2012, the malware is typically distributed via malspam campaigns and gives a remote attacker complete control over a Windows, macOS, or Linux system. It also comes with password-stealing and keylogging capabilities.
The U.S. Department of Justice (DoJ) said an investigation into the malware operation was launched by the Federal Bureau of Investigation (FBI) in 2020, with the agency creating an account on the site and paying for a subscription to create a custom NetWire RAT instance.
Are you aware of the risks associated with third-party app access to your company's SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
RESERVE YOUR SEATNetWire, over the past year, has been used by multiple threat actors, including TA2541 and OPERA1ER, to break into targets of interest and harvest sensitive information. According to Avast, it also emerged as one of the most prevalent RATs during Q4 2022.
"By removing the Netwire RAT, the FBI has impacted the criminal cyber ecosystem," Donald Alway, the assistant director in charge of the FBI's Los Angeles field office, said in a statement.
"The global partnership that led to the arrest in Croatia also removed a popular tool used to hijack computers in order to perpetuate global fraud, data breaches and network intrusions by threat groups and cyber criminals."
Source: thehackernews.com
 Reviewed by Zion3R
on
6:32 AM
Rating:
Reviewed by Zion3R
on
6:32 AM
Rating: