Paperbug Attack: New Politically-Motivated Surveillance Campaign In Tajikistan
A little-known Russian-speaking cyber-espionage group has been linked to a new politically-motivated surveillance campaign targeting high-ranking government officials, telecom services, and public service infrastructures in Tajikistan.
The intrusion set, dubbed Paperbug by Swiss cybersecurity company PRODAFT, has been attributed to a threat actor known as Nomadic Octopus (aka DustSquad).
"The types of compromised machines range from individuals' computers to [operational technology] devices," PRODAFT said in a deep dive technical report shared with The Hacker News. "These targets make operation 'Paperbug' intelligence-driven."
The ultimate motive behind the attacks is unclear at this stage, but the cybersecurity firm has raised the possibility that it could be the work of opposition forces within the country or, alternatively, an intelligence-gathering mission carried out by Russia or China.
Nomadic Octopus first came to light in October 2018 when ESET and Kaspersky detailed a series of phishing attacks mounted by the actor against several countries in Central Asia. The group is estimated to have been active since at least 2014.
The cyber offensives have involved the use of custom Android and Windows malware to strike a mix of high-value entities like local governments, diplomatic missions, and political bloggers, raising the possibility that the threat actor is likely involved in cyber surveillance operations.
The Windows malware, dubbed Octopus and which masqueraded as an alternative version of the Telegram messaging app, is a Delphi-based tool that allows the adversary to surveil victims, siphon sensitive data, and gain backdoor access to their systems via a command-and-control (C2) panel.
A subsequent analysis by Gcow Security in December 2019 highlighted the advanced persistent threat (APT) group's attacks against the Ministry of Foreign Affairs of Uzbekistan to deploy Octopus.
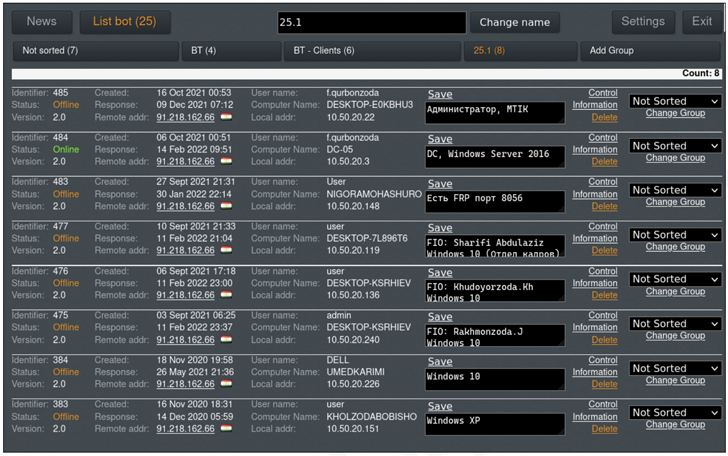
PRODAFT's findings are the result of the discovery of an operational environment managed by Nomadic Octopus since 2020, making Paperbug the first campaign orchestrated by the group since Octopus.
According to data gathered by the company, the threat actor managed to gain access to a telecommunication firm network, before moving laterally to over a dozen targets focusing on government networks, executives, and OT devices with publicly known vulnerabilities. Exactly how and when the telecommunication network was infiltrated is unknown.
"Operation PaperBug aligns with the common trend of attacking into Central Asia government infrastructure that recently became more prominent," PRODAFT noted.
Nomadic Octopus is believed to exhibit some level of cooperation with another Russian nation-state actor known as Sofacy (aka APT28, Fancy Bear, Forest Blizzard, or FROZENLAKE), based on victimology overlaps.
The latest attacks further entailed the use of an Octopus variant that comes with features to take screenshots, run commands remotely, and download and upload files to and from the infected host to a remote server. One such artifact was uploaded to VirusTotal on April 1, 2021.
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
Save My Seat!A closer look at the command-and-control (C2) server reveals that the group managed to successfully backdoor a total of 499 systems as of January 27, 2022, some of which include government network devices, gas stations, and a cash register.
The group, however, doesn't seem to possess advanced toolsets or be too concerned about covering their tracks on victim machines despite the high-stakes nature of the attacks.
"As they operate on the compromised machines to steal information, they sometimes inadvertently caused permission pop-ups on victim computers, which resulted in suspicion from the victim," the company pointed out. "However, this was resolved due to the group diligently naming the files they transfer as benign and inconspicuous programs."
The same tactic extends to naming their malicious tools as well, what with the group camouflaging them as popular web browsers such as Google Chrome, Mozilla Firefox, and Yandex to fly under the radar.
That having said, Paperbug attack chains are largely characterized by the use of public offensive tools and generic techniques, effectively acting as a "cloak" for the group and making attribution a lot more challenging.
"This imbalance between the operator skills and importance of the mission might indicate that the operators have been recruited by some entity which provided them a list of commands that need to be executed on each machine exactly," PRODAFT said, adding "the operator follows a checklist and is forced to stick to it."
Source: thehackernews.com
 Reviewed by Zion3R
on
7:09 AM
Rating:
Reviewed by Zion3R
on
7:09 AM
Rating: