PrivKit - Simple Beacon Object File That Detects Privilege Escalation Vulnerabilities Caused By Misconfigurations On Windows OS
PrivKit is a simple beacon object file that detects privilege escalation vulnerabilities caused by misconfigurations on Windows OS.
PrivKit detects following misconfigurations
Checks for Unquoted Service Paths Checks for Autologon Registry Keys Checks for Always Install Elevated Registry Keys Checks for Modifiable Autoruns Checks for Hijackable Paths Enumerates Credentials From Credential Manager Looks for current Token PrivilegesUsage
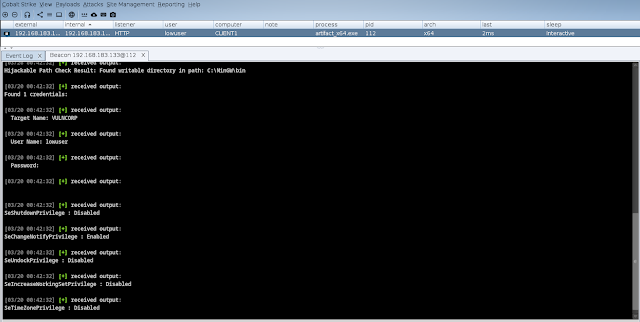
[03/20 00:51:06] beacon> privcheck[03/20 00:51:06] [*] Priv Esc Check Bof by @merterpreter[03/20 00:51:06] [*] Checking For Unquoted Service Paths..[03/20 00:51:06] [*] Checking For Autologon Registry Keys..[03/20 00:51:06] [*] Checking For Always Install Elevated Registry Keys..[03/20 00:51:06] [*] Checking For Modifiable Autoruns..[03/20 00:51:06] [*] Checking For Hijackable Paths..[03/20 00:51:06] [*] Enumerating Credentials From Credential Manager..[03/20 00:51:06] [*] Checking For Token Privileges..[03/20 00:51:06] [+] host called home, sent: 10485 bytes[03/20 00:51:06] [+] received output:Unquoted Service Path Check Result: Vulnerable service path found: c:\program files (x86)\grasssoft\macro expert\MacroService.exeSimply load the cna file and type "privcheck"
If you want to compile by yourself you can use:
make all
or
x86_64-w64-mingw32-gcc -c cfile.c -o ofile.o
If you want to look for just one misconf you can use object file with "inline-execute" for example
inline-execute /path/tokenprivileges.o
Acknowledgement
Mr.Un1K0d3r - Offensive Coding Portal
https://mr.un1k0d3r.world/portal/
Outflank - C2-Tool-Collection
https://github.com/outflanknl/C2-Tool-Collection
dtmsecurity - Beacon Object File (BOF) Creation Helper
https://github.com/dtmsecurity/bof_helper
Microsoft :)
https://learn.microsoft.com/en-us/windows/win32/api/
HsTechDocs by HelpSystems(Fortra)
https://hstechdocs.helpsystems.com/manuals/cobaltstrike/current/userguide/content/topics/beacon-object-files_how-to-develop.htm
Source: www.kitploit.com
 Reviewed by Zion3R
on
6:52 AM
Rating:
Reviewed by Zion3R
on
6:52 AM
Rating: