North Korea's Lazarus Group Suspected In $31 Million CoinEx Heist
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation of its hacks.
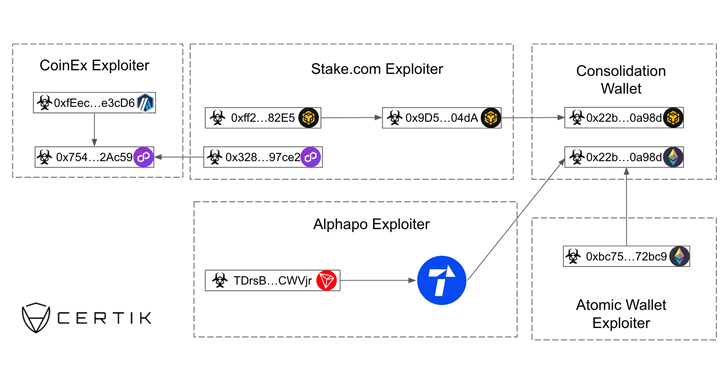
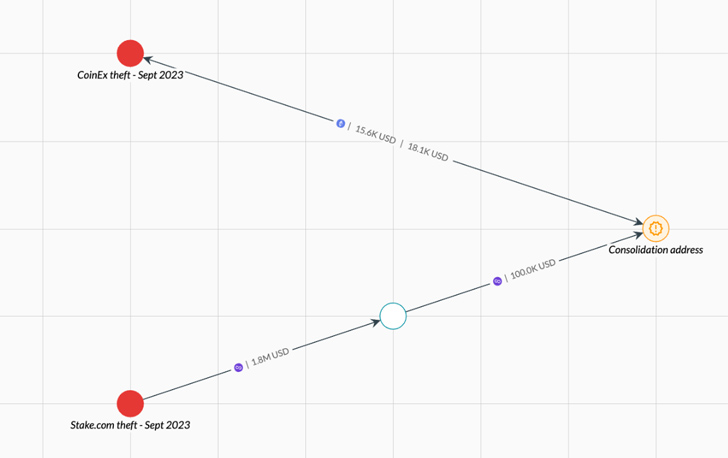
According to multiple reports from Certik, Elliptic, and ZachXBT, the infamous hacking group is said to be suspected behind the theft of $31 million in digital assets from the CoinEx exchange on September 12, 2023.
The crypto heist aimed at CoinEx adds to a string of recent attacks targeting Atomic Wallet ($100 million), CoinsPaid ($37.3 million), Alphapo ($60 million), and Stake.com ($41 million).

"Some of the funds stolen from CoinEx were sent to an address which was used by the Lazarus group to launder funds stolen from Stake.com, albeit on a different blockchain," Elliptic said. "Following this, the funds were bridged to Ethereum, using a bridge previously used by Lazarus, and then sent back to an address known to be controlled by the CoinEx hacker."
The blockchain analytics firm said the latest attacks are an indication that the adversarial collective is shifting its focus from decentralized services to centralized ones, the latter of which were its targets prior to 2020.
The pivot is likely motivated by improvements in smart contract auditing and development standards in the DeFi space and increased access offered by centralized exchanges via social engineering attacks.
The development comes as the leader of the sanctions-hit nation, Kim Jong Un, visited Russia for what's believed to be an arms deal, even as it fired two short-range ballistic missiles toward its eastern seas earlier in the week.
North Korea has leveraged cryptocurrency thefts as a way to get around sanctions and fund its weapons programs. Another revenue generation channel is its use of freelance IT workers abroad using fraudulent identification documents that obscure their true nationality.
"In recent years, there has been a marked rise in the size and scale of cyber attacks against cryptocurrency-related businesses by North Korea," TRM Labs said in June 2023. "This has coincided with an apparent acceleration in the country's nuclear and ballistic missile programs."
Dive deep into the future of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why identity is the new endpoint. Secure your spot now.
Supercharge Your SkillsThe Lazarus Group and its sub-clusters as well as other hacking outfits linked to the country have been on a rampage in recent months, orchestrating a variety of malicious operations, including software supply chain attacks targeting companies such as 3CX and JumpCloud as well as open-source repositories for JavaScript and Python.
In a post-mortem of the hack, CoinsPaid disclosed that phony recruiters from crypto companies contacted its employees via LinkedIn and various Messengers with lucrative salaries and trick them into "installing the JumpCloud Agent or a special program to complete a technical task," a campaign known as Operation Dream Job.
Source: thehackernews.com
 Reviewed by Zion3R
on
12:41 AM
Rating:
Reviewed by Zion3R
on
12:41 AM
Rating: