34 Cybercriminals Arrested In Spain For Multi-Million Dollar Online Scams
Spanish law enforcement officials have announced the arrest of 34 members of a criminal group that carried out various online scams, netting the gang about €3 million ($3.2 million) in illegal profits.
Authorities conducted searches across 16 locations Madrid, Malaga, Huelva, Alicante, and Murcia, seizing two simulated firearms, a katana sword, a baseball bat, €80,000 in cash, four high-end vehicles, and computer and electronic material worth thousands of euros.
The operation also uncovered a database with cross-referenced information on four million people that was collated after infiltrating databases belonging to financial and credit institutions.
The scams, which were conducted via email, SMS, and phone calls, entailed the threat actors masquerading as banks and electricity supply companies to defraud victims, in some cases even perpetrating "son in distress" calls and manipulating delivery notes from technology firms.
In one instance, the miscreants reportedly took advantage of a member's position in a multinational technology firm to divert computer and electronic products from suppliers to the criminal entity.
In another scam, the fraudsters gained unauthorized access to customer databases at financial institutions, added funds to customer accounts, and then contacted them to inform them of a supposed erroneous deposit, which they had to pay back by clicking on a bogus link that captured their credentials.
The cybercrime network is also alleged to have made money from offering for sale fake websites of banks, mass message programs, and collected information through specialized forums.
"The leaders of the network used false documentation, made use of spoofing techniques to hide their identity and invested their profits in crypto assets," the agency said.
The development comes months after the Spanish National Police arrested 55 individuals of a Barcelona-based group known as the Black Panthers, who were accused of taking over bank accounts by SIM swapping, stealing about €250,000 from nearly 100 people.
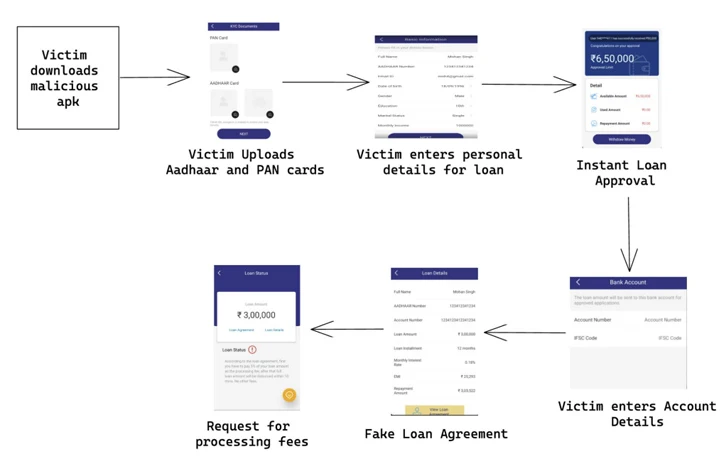
It also follows the discovery of a new money laundering scheme in which China-based scammers are using a combination of counterfeit instant loan apps and India's Unified Payments Interface (UPI) to deceive victims into parting with their funds, according to CloudSEK.
The scam involves creating instant loan Android apps that when installed by victims, seek out their personal and financial information, not to mention coerce them into granting intrusive permissions to extract sensitive data stored in the devices.
"UPI service providers currently operate without coverage under the Prevention of Money Laundering Act (PMLA)," security researchers Sparsh Kulshrestha and Bhavik Malhotra said. "Scammers manipulate mobile numbers associated with victim accounts to initiate illegal transactions."
Source: thehackernews.com
 Reviewed by Zion3R
on
5:11 AM
Rating:
Reviewed by Zion3R
on
5:11 AM
Rating: