U.S. Treasury Targets Russian Money Launderer In Cybercrime Crackdown
The U.S. Department of the Treasury imposed sanctions against a Russian woman for taking part in the laundering of virtual currency for the country's elites and cybercriminal crews, including the Ryuk ransomware group.
Ekaterina Zhdanova, per the department, is said to have facilitated large cross border transactions to assist Russian individuals to gain access to Western financial markets and circumvent international sanctions.
"Zhdanova utilizes entities that lack Anti-Money Laundering/Combatting the Financing of Terrorism (AML/CFT) controls, such as OFAC-designated Russian cryptocurrency exchange Garantex Europe OU (Garantex)," the treasury department said last week.
"Zhdanova relies on multiple methods of value transfer to move funds internationally. This includes the use of cash and leveraging connections to other international money laundering associates and organizations."
It's worth noting that Garantex was previously sanctioned by the U.S. in April 2022, coinciding with the takedown of the dark web marketplace known as Hydra.
Zhdanova has also been accused of offering services to individuals connected with the Russian Ryuk ransomware group, laundering over $2.3 million of suspected victim payments on behalf of a Ryuk ransomware affiliate in 2021.
Ryuk, a predecessor to the Conti ransomware, first emerged on the threat landscape in 2018, and has compromised governments, academia, healthcare, manufacturing, and technology organizations worldwide.
Earlier this February, a 30-year-old Russian citizen named Denis Mihaqlovic Dubnikov pleaded guilty in the U.S. to money laundering charges and for attempting to conceal the source of funds obtained in connection with Ryuk ransomware attacks.
Ransomware Continues to Evolve
The development comes as a record 514 ransomware victims were reported for the month of September 2023, registering a 153% increase year-over-year, and up from 502 in July and 390 in August.
Nearly 100 of those attacks have been attributed to nascent groups like LostTrust and RansomedVC. Some of the other new entrants observed in recent months include Dark Angels, Knight, Money Message, and Good Day.
"The record levels of ransomware attacks are partially the result of the emergence of new threat actors including RansomedVC," NCC Group said late last month.
"RansomedVC operates as 'penetration testers.' However, its approach to extortion also incorporates the claim that any vulnerabilities discovered in their targets' network will be reported in compliance with Europe's General Data Protection Regulation (GDPR).
The influx of new groups demonstrates the evolving ransomware landscape, even as more established threat actors continue to adapt and refine their tactics and techniques to dodge security controls.
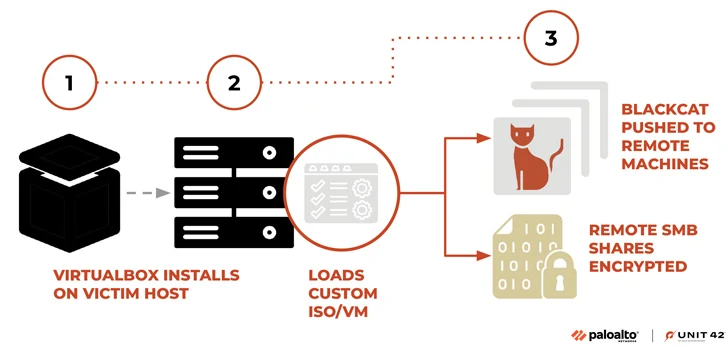
Last month, Palo Alto Networks Unit 42 reported BlackCat's addition of a utility codenamed Munchkin to its arsenal in order to propagate the ransomware payload to remote machines and shares on a victim organization network.
"This tooling provided a Linux-based operating system (OS) running Sphynx," Unit 42 researchers said. "Threat operators can use this utility to run BlackCat on remote machines, or to deploy it to encrypt remote Server Message Block (SMB)/Common Internet File Shares (CIFS)."
The diversification of ransomware is evidenced by the fact that hacktivist collectives such as GhostSec – which is part of The Five Families – have entered the fray, releasing a custom locker called GhostLocker for financial gain.
"Even if GhostLocker is not successful in the [ransomware-as-a-service] market, it seems obvious that it is a turning point as a model," SOCRadar said. "The fact that it is relatively low-priced, works with a very low percentage basis, and is accessible to almost everyone can increase ransomware attacks to severe levels."
Cybersecurity firm Uptycs, in its own analysis of GhostSec and GhostLocker, described the move as a "surprising departure from their past activities and stated agenda," given the collective's history of targeting Israeli entities in support of Palestine.
The spike in ransomware attacks has also prompted an alliance of 50 countries, called the International Counter Ransomware Initiative, pledged never to pay ransom demands in a bid to discourage financially motivated actors and ransomware gangs from profiting off such schemes.
"To shield against ransomware, it is imperative to adopt a comprehensive defense strategy," Uptycs said. "This strategy should encompass resilient backup systems, effective security software, user training, and a proactive incident response plan."
Source: thehackernews.com
 Reviewed by Zion3R
on
10:13 PM
Rating:
Reviewed by Zion3R
on
10:13 PM
Rating: