Applying The Tyson Principle To Cybersecurity: Why Attack Simulation Is Key To Avoiding A KO
Picture a cybersecurity landscape where defenses are impenetrable, and threats are nothing more than mere disturbances deflected by a strong shield. Sadly, this image of fortitude remains a pipe dream despite its comforting nature. In the security world, preparedness is not just a luxury but a necessity. In this context, Mike Tyson's famous adage, "Everyone has a plan until they get punched in the face," lends itself to our arena - cyber defenses must be battle-tested to stand a chance.
Tyson's words capture the paradox of readiness in cybersecurity: too often, untested cyber defenses can create a false sense of security, leading to dire consequences when real threats land a blow. This is where Breach and Attack Simulation (BAS), a proactive tool in any organization's cybersecurity arsenal, comes into play.
When Cybersecurity Meets the Punch - The Assumption Problem
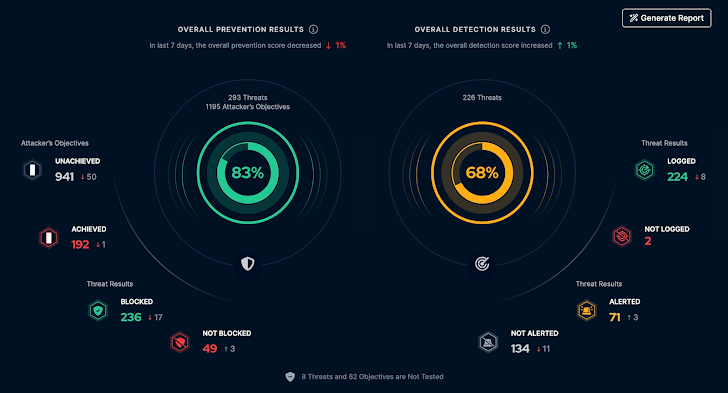
Assumptions are the hidden icebergs in cybersecurity's vast ocean. Although we might believe our security controls are foolproof, the statistics paint another picture. According to the Blue Report 2023 by Picus, only 59% of attacks are prevented, just 37% detected, and a scant 16% triggered alerts. This data reveals an alarming truth: cybersecurity measures often fall short in real-world scenarios. Oftentimes, this shortcoming is due to complexities in configuration and a shortage of skilled professionals, which can lead to underperforming and misconfigured defenses. At the same time, traditional testing methods like penetration tests and red team exercises can't fully gauge the effectiveness of an organization's security. This can contribute to the often dangerous assumption that security controls are effective without continuously stress-testing them in real-world scenarios.
This chasm between perceived and actual security confirms the growing need for security validation through Breach and Attack Simulation (BAS) - a method of confronting these fallacies by rigorously validating defenses before attacks catch organizations off guard. Ultimately, BAS tightens the veil of cybersecurity across every potential breach.
Shifting the Mindset from Plan to Practice
Cultivating a proactive cybersecurity culture is akin to shadowboxing, putting theory into motion. Cyber threats morph as swiftly as clouds in a stormy sky, and simulations must be as dynamic as the threats they mimic. This cultural shift begins at the top, with leadership championing the embrace of continuous security validation through BAS. Only then can cybersecurity teams embed this practice-centric philosophy, sparring with simulations frequently and with intent.
The Mechanics of BAS
BAS is a reality check for your cybersecurity posture. At its core, BAS is the systematic, controlled simulation of cyberattacks across your production network. Each simulation is designed to mimic the behavior of actual attackers, cultivating preparedness for adversary tactics, techniques, and procedures (TTPs). According to the Red Report 2023, threat actors use an average of 11 different TTPs during an attack.
For example, an APT attack scenario begins with initial breach methods, such as exploiting software vulnerabilities or phishing emails with malicious attachments. Then, it moves deeper, attempting lateral movements within the network, escalating privileges where possible, and trying to exfiltrate simulated sensitive data. In this scenario, the objective is to replicate an entire attack lifecycle with fidelity, all while analyzing how your security controls respond at each step.
What's more, BAS isn't just a one-off exercise. It's an ongoing process that adapts as the threat landscape evolves. As new malware variants, TTPs, exploit techniques, APT campaigns, and other emerging threats come to light, they are incorporated into the BAS tool's threat intelligence library. This ensures that your organization can defend itself against the potential threats of today and tomorrow.
Following each simulation, BAS tools provide comprehensive analytics and insightful reports. These contain crucial details on how the intrusion was (or wasn't) detected or prevented, the time it took for the security controls to respond, and the effectiveness of the response.
Armed with this data, cybersecurity professionals can better prioritize their response strategies, focusing on the most pressing gaps in their organizational defense first. They can also fine-tune existing security controls with easy-to-apply prevention signatures and detection rules that can improve their ability to detect, prevent, or react to cyber threats.
Integrating the BAS Punch into Your Cyber Strategy
Imagine that BAS is a consistent pulse reinforcing your security measures. Effectively incorporating BAS into your organization's defenses begins with critical analysis to determine how it complements your cybersecurity architecture.
Step 1: Tailor BAS to Your Needs
Customizing BAS for your organization starts with understanding the threats you're most likely to face - because a bank's primary cybersecurity concerns differ from a hospital's. Choose simulations that reflect the most relevant threats to your industry and technical infrastructure. Modern BAS tools can generate customized simulation playbooks with cyber threats most likely to affect your organization.
Step 2: Create a Simulation Schedule
Consistency is key. Run BAS simulations regularly, not just as a one-time event but as an integral part of your cybersecurity strategy. Establish a cadence - whether daily, weekly, monthly, or in real-time following significant IT or threat landscape changes - to remain a step ahead of adversaries who continuously refine their tactics.
Step 3: Apply the Insights
The true value of BAS lies in the actionable insights derived from simulation results. Advanced BAS platforms provide practical recommendations, such as prevention signatures and detection rules that can be directly incorporated into security controls - including IPS, NGFW, WAF, EDR, SIEM, SOAR, and other security solutions - to strengthen your security posture immediately.
Step 4: Measure and Refine
Define quantitative success metrics to evaluate the impact of BAS on your organization's cybersecurity. This can include the ratio of blocked/logged/alerted attacks to all attacks, the number of addressed defensive gaps, or improvements in detection and response times. Continuously refine your BAS process based on these performance indicators to ensure your defenses get sharper with each iteration.
Ready to Fortify Your Cyber Defenses with the Pioneer of BAS Technology?
As we unpack the parallels between a boxer's defense and an organization's security posture, one mantra echoes true: surviving the first punch is about resilience through relentless practice. Here, we have demonstrated the critical role BAS plays in cultivating a proactive approach to the unpredictability of cyber threats.
Picus Security pioneered Breach and Attack Simulation (BAS) technology in 2013 and has helped organizations improve their cyber resilience ever since. With Picus Security Validation Platform, your organization can expect unparalleled visibility into its security posture, so you can hone your defenses against even the most sophisticated cyberattacks.
With Picus, you're not just reacting; you're proactively countering cyber threats before they impact your operations. Organizations must throw the first punch, challenging and strengthening their defenses for when the real fight begins. So, gear up; it's time to put your cyber defenses to the test. Visit us at picussecurity.com to book a demo or explore our resources.
Note: This article was written by Dr. Suleyman Ozarslan, co-founder and VP of Picus Labs at Picus Security, where simulating cyber threats and empowering defenses are our passions.
Source: thehackernews.com
 Reviewed by Zion3R
on
4:30 AM
Rating:
Reviewed by Zion3R
on
4:30 AM
Rating: